Download the latest CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes in PDF format. These Class 10 Computer Science revision notes are carefully designed by expert teachers to align with the 2025-26 syllabus. These notes are great daily learning and last minute exam preparation and they simplify complex topics and highlight important definitions for Class 10 students.
Chapter-wise Revision Notes for Class 10 Computer Science Chapter 4 Web Applications and Security
To secure a higher rank, students should use these Class 10 Computer Science Chapter 4 Web Applications and Security notes for quick learning of important concepts. These exam-oriented summaries focus on difficult topics and high-weightage sections helpful in school tests and final examinations.
Chapter 4 Web Applications and Security Revision Notes for Class 10 Computer Science
A web application (web app) is an application program that is stored on a remote server and delivered over the Internet through a browser interface.
Common web applications include web mail, online retail sales and online auction, etc.
Security is fundamentally about protecting assets (data, hardware, reputation, etc.). Therefore, you should
- Identify potential threats
Know how to react to an attack
- Detect and fix vulnerabilities
Working with Accessibility Options
Accessibility features are designed to help people with disabilities so that they use technology more easily. For example, a text-to-speech feature may read text out loud for people with limited vision, while a speech-recognition feature allows users with limited mobility to control the computer with their voice.
Launching Accessibility Options
To launch accessibility options, follow the given steps
Step 1 Click on Start button→ Control Panel. Control Panel window will appear on your screen with various categories.
Step 2 Click on Ease of Access category. After this, Ease of Access window will appear.
Step 3 In the Ease of Access Center, click on Let Windows suggest settings.
Step 4 A window will provide in which you can change settings of keyboard, mouse etc.
Step 5 You can choose any options under Select all statements that apply to you.
Step 6 Click on Ease of Access Center. A window will appear.
Step 7 In this window, four options are given as
- Start Magnifier a display utility that makes the computer screen more readable by creating a separate window that displays a magnified portion of the screen.
- Start Narrator a text-to-speech utility that reads what is displayed on the screen–the contents of the active window.
- Start On-Screen Keyboard displays a virtual keyboard on the computer screen that allows people to type data by using a pointing device.
- Set up High Contrast a window showing settings for color and contrast of display.
Explore All Settings
Instead of looking for accessibility settings in various places on your computer, Windows bring all those settings together and organises them into categories that you can explore in Ease of Access Center. Some of them are
(i) Make the Computer Easier to See
If you occasionally have trouble seeing items on your screen, you can adjust the settings to make text and images on the screen appear larger, improve the contrast between items on the screen.
You can adjust many of these settings on the Make the computer easier to see page in the Ease of Access Center.
Open the Ease of Access Center, then select the options that you want to use.
- Choose High Contrast This allows you to set a highcontrast color scheme that heightens the color contrast of some text and images on your computer screen.
- Remove Background Images This turns off all unimportant, overlapped content and backgroup images to help make the screen easier to use.
(ii) Make the Mouse Easier to Use
You can change how the mouse pointer looks and turn on other features that can help make it easier to use your mouse.You can adjust these settings on the Make the mouse easier to use page in the Ease of Access Center.
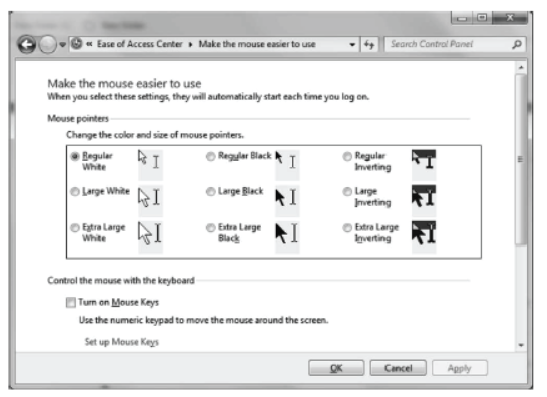
You can
- Change the Color and Size of Mouse Pointer You can use these options to make the mouse pointer larger or change the color to make it easier to see.
- Turn on Mouse Keys You can use this option to control the movement of the mouse pointer by using the numeric keypad.
(iii) Make the Keyboard Easier to Use
You can use your keyboard to control the mouse and make it easier to type certain key combinations. You can adjust these settings on the Make the keyboard easier to use page in the Ease of Access Center.
You can
- Turn on Sticky Keys This option sets Sticky Keys to run when you log on to windows. Instead of having to press three keys at once (Ctrl, Alt, Delete), you can use one key by turning on Sticky Keys and adjust settings.
- Turn on Toggle Keys This option sets Toggle Keys to run when you log on to windows. These keys can play an alert each time you press the Caps Lock, Num Lock or Scroll Lock Keys.
(iv) Use Text or Visual Alternatives to Sounds
Windows provide settings for using visual cues to replace sounds in many programs.
You can adjust these settings on the use text or visual alternatives for sounds page in the Ease of Access Center.
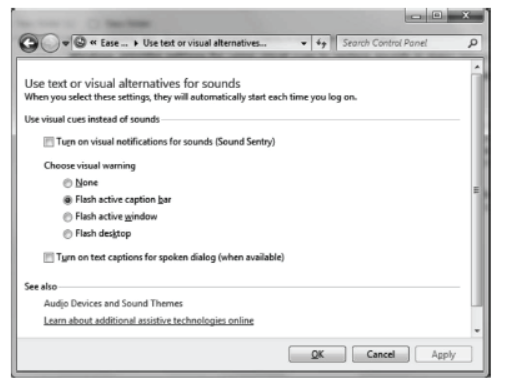
You can
- Turn on Visual Notifications for Sounds This option sets sound notifications to run when you log on the Windows. You can also choose how you want sound notifications to warn you.
- Turn on Text Captions for Spoken Dialog This option causes windows to display text captions in place of sounds to indicate that activity is happening on your computer.
Networking Fundamentals
A network can be defined as an interconnected collection of autonomous computers. A ‘computer network’ or simply a ‘network’ is a collection of computers and other hardware devices, interconnected by communication channels (satellites or cables) that allow sharing of resources and information. A computer networking is the practice for exchanging informations/services between two or more computer devices together for the purpose of sharing data. The speed of a network is measured in Mbps (Megabits per second).
Benefits of Networking
Computer network is very useful in modern environment, so some of the benefits of networking are discussed here :
- File Sharing Networking of computers helps the users to share data files.
- Hardware Sharing Users can share devices such as printers, scanners, CD-ROM drives, hard drives, etc.
- Application Sharing Applications can be shared over the network and this allows to implement client/server applications.
- User Communication This allows users to communicate using E-mail, newsgroups, video conferencing within the network.
- Access to Remote Database By networking, we are able to access to the remote database. It is easy for any person using his PC tomake reservations for aeroplanes, trains, hotels, etc., anywhere in the world with instant confirmation within the network.
Types of Network
A network refers to a group of interconnected computerswhich are capable of sharing information and communication devices. On the basis of coverage or geographical spread, a network can be divided into following types:
LAN (Local Area Network)
When a group of computers and its devices are connected in a small area, then this network is said to be a LAN. Computers or users in a local area network can share data, information, software and common hardware devices such as printer, modem, hard disk, etc. A LAN typically relies mostly on wired connections for increased speed and security but wireless connection also be a part of LAN. LAN are used within office building, school, etc.
MAN (Metropolitan Area Network)
This is basically bigger version of LAN and normally uses similar technology. It might cover few buildings in a city and might either be private or public. e.g. In a city, a MAN, which can support both data and voice might even be related to local cable television network.
WAN (Wide Area Network)
The network which connects the different countries network is known as WAN. It can be a group of LANs. The largest existing WAN is Internet. For example, a network of ATMs, BANKs, National Government Offices spread over a country or continents are examples of WANs.
Comparison between LAN, MAN and WAN
| Basis | LAN | MAN | WAN |
| Speed | 11 to 54 Mbps | 11 to 100 + Mbps | 10 to 384 Kbps, 1.83 to 7.2 Mbps |
| Range | Upto 5 km | 5 km to 15 km | Upto 1000km |
| Applications | Enterprise networks | Even replacement last mile access | Mobile phones, Cellular data |
PAN (Personal Area Network)
PAN refers to a small network of communication. The range of a PAN is generally 10 metre. PAN may be wired using USB cables or wireless using wireless network technologies such as bluetooth, wireless USB, 2-wave and ZigBee. Bluetooth personal area network is also called a piconet. It can be composed of upto eight devices in a master–slave relationship.
Network Devices
Network devices are the components used to connect computer and other electronic devices together, so that they can share files or resources like printers or fax machines. The most common type of network devices used by the public to set-up a Local Area Network (LAN) are hub, switch, repeater and if online access is desired, a high-speed modem is required.
Some of them are described below
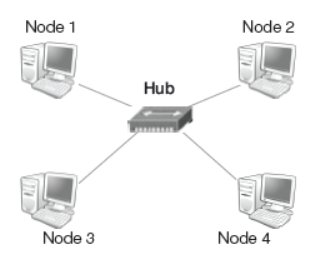
Hub
A hub is a device, which is used with computer systems to connect several computers together. It acts as a centralised connection to several computers with the central node or server. It is a multi-port device, which provides access to computers.
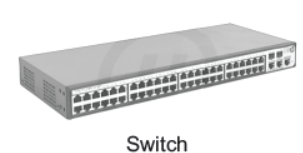
Switch
A switch is a hardware device, which is used to connect devices or segment of network with smaller subsets of LAN segments. The main purpose of segmenting is to prevent the traffic overloading in a network.
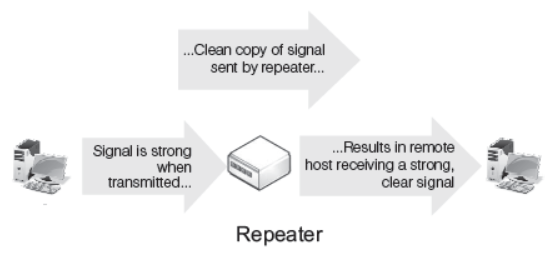
Repeater
Repeater is a hardware device, used to amplify the feeble signals, when they are transported over a long distance. When the signal is transmitted over a line, then due to resistance and other causes it accumulates noise. Due to this noise, the quality of signal degrades. The basic function of a repeater is to amplify the incoming signal and retransmit it to the other device.
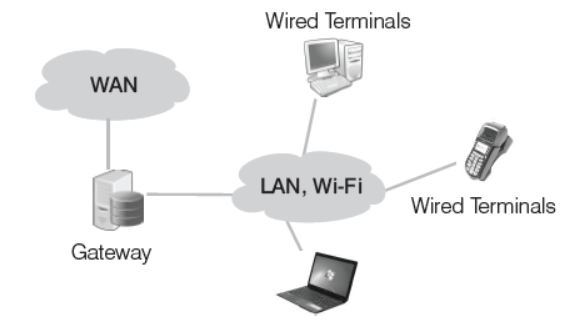
Gateway
A gateway is a device which is used to connect dissimilar networks. The gateway establishes an intelligent connection between a local network and external networks, which are completely different in structure. Infact, the gateway is a node that routes the traffic from a workstation to outside network.
The gateway also acts as a proxy server and a firewall, which prevents the unauthorised access.
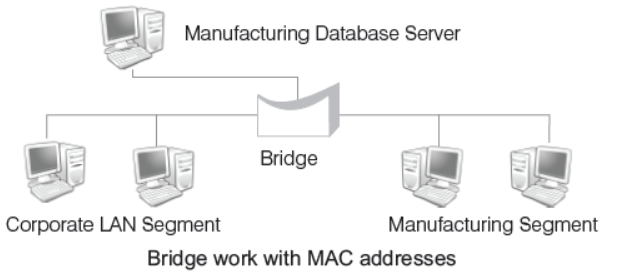
Bridge
Bridge serves a similar function as switches. A bridge filters data traffic at a network boundary. Bridge reduces the amount of traffic on a LAN by dividing it into two segments. Traditional bridge supports one network boundary, whereas switches usually offer four or more hardware ports. Switches are sometimes called multi-part bridges
Router
A hardware device designed to take incoming packets, analyse the packets, move the packets to another network, convert the packets to another network interface, drop the packets, direct packets to the appropriate locations, etc. A router functions similar to a bridge. However, unlike a bridge, a router passes data packets from one network to another network based on their IP addresses not MAC addresses.
Modem (Modulator/Demodulator)
Modem is a device that converts digital signal to analog signal (modulator) at the sender’s site and converts back analog signal to digital signal (demodulator) at the receiver’s end, in order to make communication possible via telephone lines.
NIC (Network Interface Card)
NIC provides the physical connection between the network and the computer workstation. With most LAN’s cables, NIC is used for their connectivity.
Network Topologies
The network topology refers to the arrangement or pattern of computers, which are interconnected in a network. Commonly used network topologies are as follows
Bus Topology
It is a type of network in which the computers and the peripheral devices are connected to a common single length data line.
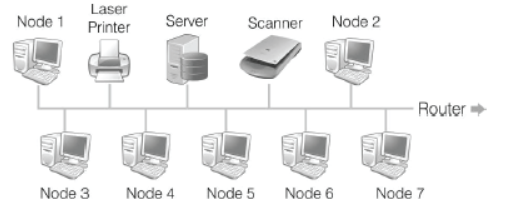
All the computers or devices are directly connected to the data line. The data is transmitted in small blocks, known as packets.
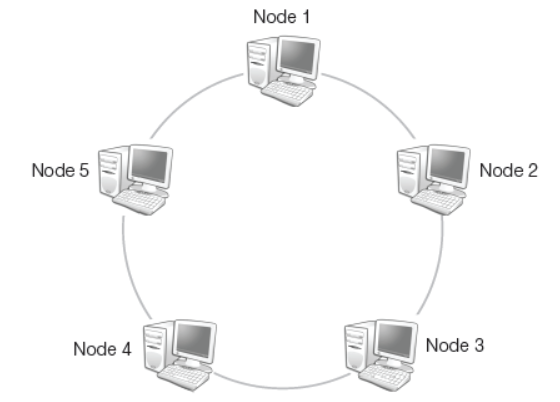
Ring or Circular Topology
In this type of topology, each node is connected to two and only two neighbouring nodes. The data travels in one direction only from one node to another node around the ring. After passing through each node, the data returns to the sending node.
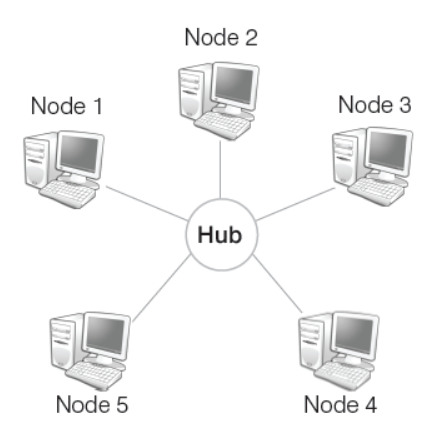
Star Topology
In this topology, there persists a central node called server or hub, which is connected to the nodes directly. If a node has to take information from other node, then the data is taken from that node through the central node or server.
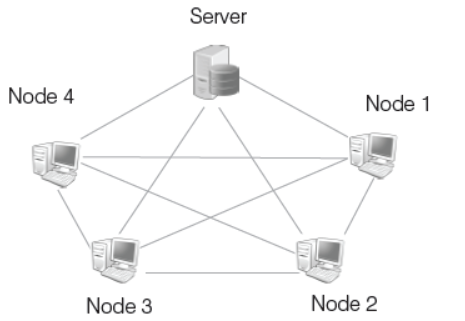
Mesh Topology
In this topology, each node is connected to more than one node, so that it provides alternative route, in case, if the host is either down or busy. It is also called a completely interconnected network. We can also call it as an extension to P2P network.
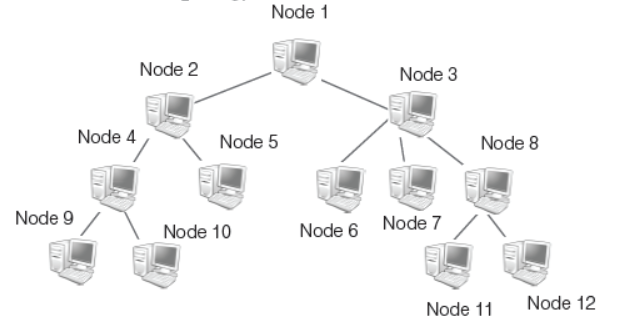
Tree Topology
It is an extension and variation of bus topology. Its basic structure is like an inverted tree, where the root acts as a server. In tree topology, the node is interlinked in the form of tree. If one node fails, then the node following that node gets detached from the main tree topology.
Models of Computer Networking
There are mainly two models of computer networking, which are as follows
(i) Peer-to-Peer Network It is also known as P2P network. This computer network relies on computing power at the edges of a connection rather than in the network itself. P2P network is used for sharing content like audio, video, data or anything in digital format. In P2P connection, a couple of computers is connected via a Universal Serial Bus (USB) to transfer files. In peer-to-peer networking, each or every computer may be worked as server or client.
(ii) Client-Server Network The model of interaction between two applications programs in which a program at one end (client) requests a service from a program at the other end (server). It is a network architecture which separates the client from the server. It is scalable architecture, where one computer works as server and others as client. Here, client acts as the active device and server behaves as passively.
Data Transfer on Network
Switching techniques are used for transmitting data across networks. Different types of switching techniques are employed to provide communication between two computers. These are
(i) Circuit Switching It is a methodology of implementing a telecommunication network in which two network nodes establish a dedicated communication channel (circuit), first through the network and then the message is transmitted through the channels. The main advantage of circuit switching is guaranteed delivery. The circuit switching guarantees the full bandwidth of the channels and remains connected for the duration of the communication session. The defining example of a circuit switched network is the early analog telephone network. When a call is made from one telephone to another, switches within the telephone exchanges create a continuous wire circuit between the two telephones for as long as the call last.
(ii) Message Switching It is a network switching technique, in which data is routed entirely from the source node to the destination node. In this technique, no physical path is established between source and destination in advance. During message routing, every intermediate switch in the network stores the whole message. If the entire network’s resources are engaged or the network becomes blocked, the message switched network stores and delays the message until some resource become available for effective transmission of the message.
(iii) Packet Switching In packet-based networks, the message gets broken into small data packets. These packets are sent out from the computer and they travel around the network seeking out the most efficient route to travel as circuits become available. This does not necessarily mean that, they seek out the shortest route. The main advantage of packet switching is that the packets from many different sources can share a line, allowing for very efficient use of the communication medium.
Internet
The Internet has gained popularity and emerged as an important and efficient means of communication. The term Internet is derived from the words ‘interconnection’ and ‘networks’. A network is a collection of two or more computers, which are connected together to share information and resources. The Internet is a world wide system of computer networks, i.e. network of networks. Through Internet, computers become able to exchange information with each other and find diverse perspective on issues from a global audience. Most of the people use Internet for sending and receiving E-mail and net surfing for retrieving information.
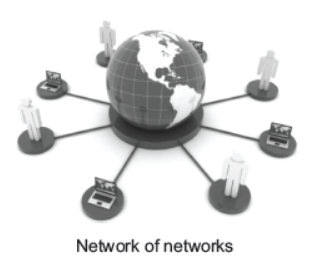
There are mainly three ways of connecting to the Internet, which are as follows
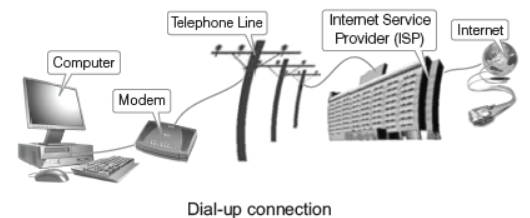
Dial-up Connection
It is a temporary connection, set-up between your computer and ISP server.
Dial-up connection uses the telephone line Public Switched Telephone Network (PSTN) and modem to connect to the Internet. The modem connects the computer through the standard phone lines, which serves as the data transfer medium. When a user initiates a dial-up connection, user needs to enter the password and specify a username and modem dials a phone number of an Internet Service Provider (ISP) to receive dial-up calls. DSL broadband service providers in India are BSNL, Airtel, Reliance, MTNL and Tata Indicom, etc. The ISP then establishes the connection, which usually takes about 10 s and is accompanied by several beeping and buzzing sounds.
Broadband Connection
The term broadband commonly refers to high speed Internet access that is always ON and faster than the traditional dial-up access. It is the short form of broadband width, that uses a telephone line to connect to the Internet. Speed of broadband connection is measured in Mbps (Megabits per second). Broadband access allows users to connect to the Internet at greater speed than a standard 256 Kbps (Kilobits per second) modem or dial-up access. Broadband access requires the use of a broadband modem.
Broadband includes several high speed transmission technologies, which are as follows
(i) Digital Subscriber Line (DSL) It is a popular broadband connection which provides Internet access by transmitting digital data over the wires of a local telephone network. It uses the existing copper telephone lines for Internet access. A special modem is necessary in order to be able to use a DSL service over a standard phone line.
Faster forms of DSL, typically available to businesses are as follows
- High data rate Digital Subscriber Line (HDSL)
- Very High data rate Digital Subscriber Line (VHDSL or VDSL)
- Asymmetrical Digital Subscriber Line (ADSL)
- Symmetrical Digital Subscriber Line (SDSL)
(ii) Cable Modem This service enables cable operators to provide broadband using the same co-axial cables, that deliver pictures and sound to your TV set. A cable modem can be added to or integrated with a set-top box that provides your TV set for Internet access. They provide transmission speed of 1.5 Mbps or more.
(iii) Broadband over Power Line (BPL) It is the delivery of broadband over the existing low and medium voltage electric power distribution network. Its speed is generally comparable to DSL and cable modem speeds. BPL can be provided to homes using existing electrical connections and outlets. It is also known as power-band. BPL is good for those areas where there are no broadband connections, but power infrastructure exists. e.g. in rural areas.
Wireless Connection
Wireless broadband connects a home or business to the Internet using a radio link between the customer’s location and the service provider’s facility. Wireless broadband can be mobile or fixed. Unlike DSL and cable, wireless broadband requires neither a modem nor cables.
The distance between the devices connected to each other through a wireless Internet connection does not affect the rate of data transfer between them. Some ways to connect the
Internet wirelessly are as follows
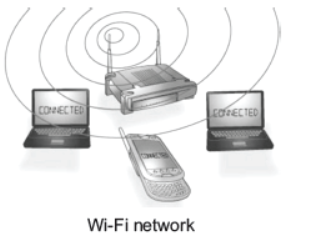
(i) Wireless Fidelity (Wi-Fi) It is a universal wireless networking technology that utilises radio frequencies to transfer data. Wi-Fi allows high speed Internet connections without the use of cables or wires. Wi-Fi networks can be designed for private access within a home or business. It can be used for public Internet access at ‘hotspots’ that offers Wi-Fi access such as restaurants, coffee shops, hotels, airports, convention centres and city parks.
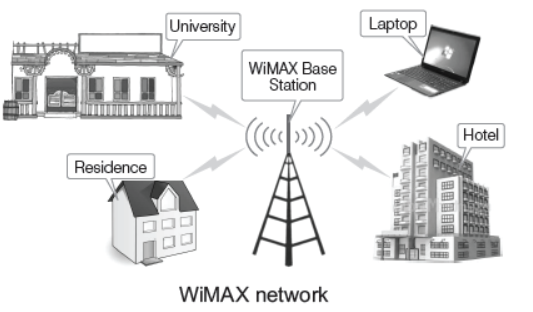
(ii) Worldwide Interoperability for Microwave Access (WiMAX) Today, it is one of the hottest broadband wireless technology. These systems are expected to deliver Broadband Wireless Access (BWA) services upto 31 miles (45 km) for fixed stations and 3-10 miles (5-15 km) for mobile stations.
WiMAX would operate similar to Wi-Fi but at higher speed, over greater distances and for a greater number of users. It has the ability to provide services even in areas that are difficult for wired infrastructure to reach. Also, it has the ability to overcome the physical limitations of traditional wired infrastructure.
Terms Related to Internet
Some terms related to Internet, which are as follows World Wide Web (WWW) It is a system of Internet servers that supports hypertext and multimedia to access several Internet protocols on a single interface. It is often abbreviated as the Web or WWW. It is a way of exchanging information between computers on the Internet, trying to tie them together into a vast collection of interactive multimedia resources. It is only a portion of what makes up the Internet, but it is the fastest growing part of the Internet.
Web Page
The backbone of theWorld Wide Web is made up of files or documents called pages or web pages, that contain information and links to resources both text and multimedia. It is created using HTML (HyperText Markup Language).
Website
A group of related web pages that follow the same theme and are connected together with hyperlinks is called a Website. In other terms, “A website is a collection of digital documents, primarily HTML files, that are linked together and that exist on the web under the same domain.” Each website is accessed by its own address known as URL (Uniform Resource Locator). e.g. http://www.carwale.com is a website, while http://www.carwale.com/new/ is a web page.
Two terms that are associated with a website are as follows
(i) Home Page The initial, main or first page of a website is known as home page. It can help the viewers to find out what they can find on particular site.
(ii) Web Portal It is a web page that combines useful information and links.
Web Browser
It is a software application that is used to locate, retrieve and display some content on the World Wide Web, including web pages. These are programs used to explore the Internet. It is an interface that helps a computer user to gain access over all the content on the Internet.We can install more than one web browsers on a single computer. The user can navigate files, folders and websites with the help of a browser. There are two types of web browsers, which are as follows
(i) Text Web Browser A web browser that displays only text-based information is known as text web browser. e.g. Lynx.
(ii) Graphical Web Browser A web browser that supports both text and graphic information is known as graphical web browser. e.g. Internet Explorer, Firefox, Netscape, Safari (for Apple), Google Chrome, Opera, etc.
Web Server
It is a computer program that serves requested HTML pages or files from the web client. A web client is the requesting program associated with the user. The web browser is a client that requests HTML files from web servers. Every web server that is connected to the Internet is associated with a unique address, i.e. IP address which is made up of a series of four numbers between 0 to 255 separated by periods. e.g. 68.178.157.132 or 68.122.35.127.
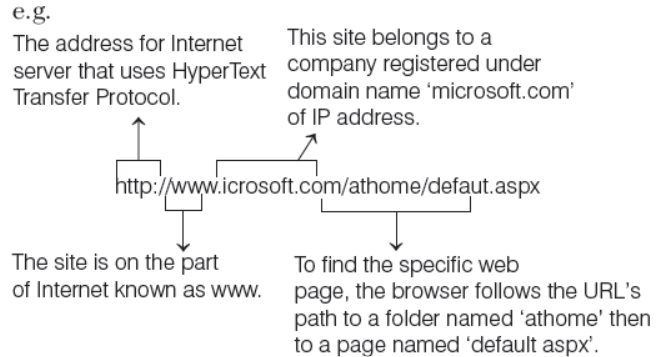
Web Address/URL
Web is a collection of documents (web pages) stored on computers around the world. Each web page has an address describing where it can be found. This address is known as web address or URL (Uniform Resource Locator). A web address identifies the location of a specific web page on the Internet, such as
http :// www. learnyoga.com
On the web, web addresses are called URLs. It is the web address for a website or a web page. The URL specifies the
Internet address of a file stored on a host computer connected to the Internet.
Parts of URL
The URL contains three parts, which are as follows:
(i) The name of the protocol to be used to access the file resource.
(ii) A domain name that identifies a specific computer on the Internet.
(iii) A path name with hierarchical description that specifies the location of a file in that computer.
E-mail Address
E-mail stands for ‘Electronic Mail’. It is a paperless method of sending messages, notes, pictures and even sound files from one place to another using the Internet as a medium. It is an individual name, which is used to send and receive E-mail on the Internet. It is used to specify the source or destination of an E-mail message.
Introduction to Instant Messaging
Instant Messaging (IM) is an Internet service that allows people to communicate with each other in real time through an instant messaging software. Unlike E-mail, instant messaging allows messages from one person to appear right away on the other person’s computer screen right after the send button is pressed. Instant Messaging allows effective and efficient communication, allowing immediate receipt of acknowledgement or reply. However, IM is basically not necessarily supported by transaction control.
Many instant messaging services offer video calling features, Voice over Internet Protocol (VoIP) and web conferencing services. Web conferencing service can integrate both video calling and instant messaging abilities.
Instant Messaging Account
Messaging to each other participants need to be signed in to the same instant messaging software. To use instant messaging software, a user must have a valid instant messaging account. These accounts are differ in formats. Some IM software such as Yahoo- Messenger, Windows live messenger use E-mail addresses for managing the account and software such as Skype use standard names.
Instant Messaging Service
Here are services of instant messaging
- Accepts instant messages from external sites.
- Determines the user to which the message should be delivered and routers it accordingly.
- Accepts instant messages from internal hosts.
- Determines the destination system to which the message should be delivered and routes it accordingly.
Key Features of an Instant Messaging
Key features of an instant messaging are as follows
- Video calling
- Language translation (IM has an in-built translator).
- Going invisible (Your status can be shown as offline to your IM contact list).
- Encrypted messages (Text sent disappears from the receiver’s phone automatically after they read it).
- In-built lock.
- Save messages for future reference.
Popular Instant Messaging Software
There are two kinds of instant messaging software, which are as follows
Application Based
This type of instant messaging software are downloaded from
Internet and installed on user’s computer. These are
- Whatsapp - Facebook Messenger
- Viber - Google Talk
- Skype - WeChat
Web Based
This type of software is accessed using browsers such as google chrome etc. These are
- Meebo - Yahoo- Web Messenger
- eBuddy - AIM Express
- MSN Web Messenger - MessengerFX
Google Talk Instant Messenger
Google Talk is also known as Gtalk, developed by Google. It is an instant messaging services that provides both text and voice communication developed by Google Inc. This is a free service from Google which requires users to have a google or gmail account to use the client.
Launching Google Talk
To launch Google Talk, follow the given steps
Step 1 Click on Start button.
Step 2 Click on All Programs. A sub menu will appear.
Step 3 Click on Google Talk and then click on Google Talk.
Or
Step 4 Double click on Google Talk icon which appear on desktop.
To Sign in, into your Google Talk Account
To sign in, into your Google Talk account, follow given step
Step 1 Use your Gmail account’s username and password.
Step 2 Then click on Sign in button to sign into Google Talk.
Chatting on Instant Messenger
Chatting on Google Talk
Here are the steps to chat with a contact on Google Talk
Step 1 You can start chatting with your contact by double click on Google Talk. After this, a pop-up window will appear on the screen.
Step 2 Chat window has text box. In this box, you can type message and press Enter key.
Step 3 Message will sent to other person. He/She will read this message and reply your message if he/she wants.
To use Group Chat, just start a conversation with a contact, then click the drop–down on the right of the chat window and select Group Chat.
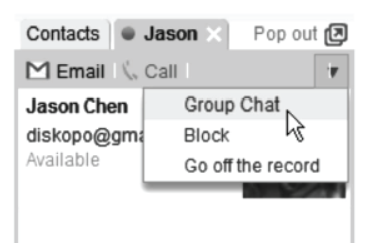
Chatting on G-mail
Besides sending and receiving E-mail, G-mail users have access to a range of additional features that can be quite useful. One of the most popular features of G-mail is chat.
Google Hangouts is Gmail’s instant messaging feature,which allows you to talk in real time to friends and family.
To chat on G-mail, follow the given steps:
Step 1 Log in to your G-mail account with username and password.
Step 2 A window will appear on the screen.
Step 3 Left side of this window, contact list will be display.
Step 4 Double click on the contact name with which you want to start chat.
Step 5 After clicking on the contact name, a small pop-up window will be displayed on the right bottom side.
Step 6 Here, you can type the message for chatting.
Chatting on Yahoo
With Yahoo Messenger, you can chat and talk with your friends with yahoo accounts easily. You can use the Yahoo Messenger program on your computer or the app on your mobile device to call your friends and talk to them.
To chat on Yahoo, follow the given steps
Step 1 Open your Yahoo account with your Yahoo id and password.
Step 2 Click your Name or Yahoo id in the upper-left corner of the screen and select Available to show your contacts that you are online and able to chat.
Step 3 Click the Minimized Yahoo Messenger window at the bottom of the screen, if it automatically appeared when you went online.
Step 4 This maximizes window and displays any requests you received since the last time you were online. Click Accept, Decline or Block to act on an add request.
Step 5 ClickComposeMessage→ Instant Message, to start a new conversation. Type a message and press Enter to send the message.
General rules and etiquettes to be followed while
chatting
- The first thing you should check is, if the person infront of you is available or busy.
- It’s simply rude to keep someone hanging, when they are expecting an answer from you. So, the polite thing would be to respond.
- Don’t use offensive language.
- Avoid replying to negative comments with more negative comments.
- You may have to leave your seat for some reason but always inform the person infront that you are going to be away for sometime.
Creating and Publishing Web Pages – Blog
A blog is a website or a web page, in which an individual records opinion links to other sites on regular basis. A blog content is written frequently and added in a chronological order. It is written online and visible to everyone. A typical blog combines text, images and links to other blogs, web pages and other media related to its topic. In education, blogs can be used as instructional resources.
These blogs are referred to as edublogs. The entries of blog are also known as posts. A person who writes a blog or a weblog is known as blogger. Blogging is the act of posting content on a blog. There are some popular websites which offer blog service as follows
- Joomla - WordPress.com
- Drupal - Blogger
- Tumblr - Weebly
Creating a Blog Account on WordPress
WordPress is a free personal publishing platform. It is an easy to use, fast and flexible blog script. It comes with a great set of features, designed to make your experience as a publisher as pleasant as possible. The steps to create a Blog account in WordPress are as follows
Step 1 Open a web browser e.g. Mozilla Firefox, Google Chrome etc., for creating a blog account.
Step 2 Type the URL www.wordpress.com in the address bar and press Enter key.
Step 3 Now, click on Sign Up button and after this, a page will appear as shown below
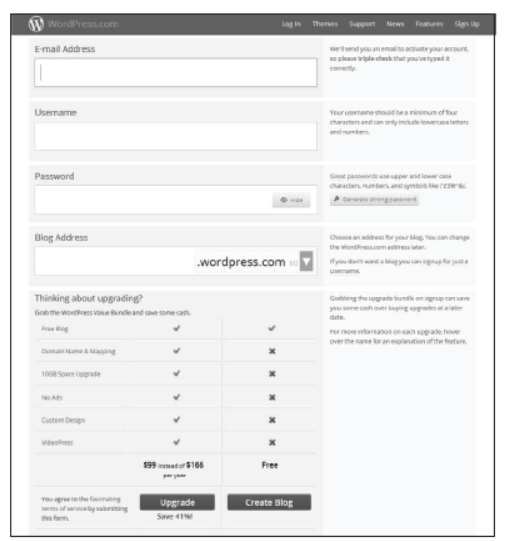
Step 4 Above page shows different fields such as E–mail Address, Username, Password etc.
- E-mail Address WordPress will sent an activation link to your e-mail id after clicking on Create Blog button.
So, provide a valid e-mail address.
- Username This name will manage your blog.
- Password You must use strong password for securing purpose. You can use uppercase and lowercase letter with numbers and special symbols.
- Blog Address This address is used by viewer to view your blog.
- Language Here, you can choose language in which you want to write a blog.
Step 5 Click on Create Blog button.
Step 6 Now, you will get an activation link on your e–mail account. Open your e–mail and check to WordPress e-mail.
Step 7 Open that e–mail and click on Confirm Now link, your blog will be activated.
Step 8 After activating the blog, WordPress Blog Account will appear on your screen.
Adding Context to the Blog
Now, your blog is ready to use. To create a post, follow the given steps
Step 1 Click on New Post from the left side of the window.
The following window will appear on the screen.
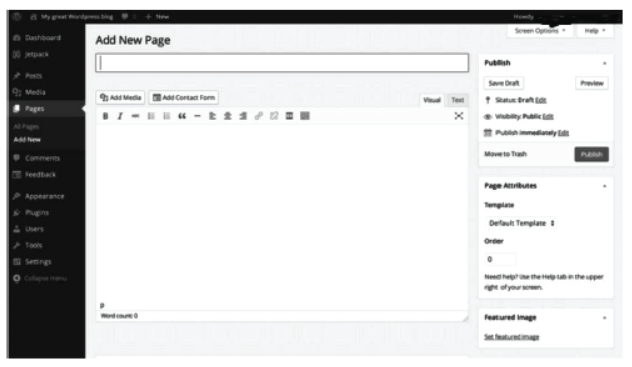
Step 2 Given the title to your blog in Add New Page text box
Step 3 Type the content in content box and click on Publish button to publish your post.
Step 4 To view your post, open the web browser and type your blog address in the address bar.
Step 5 Now, you can see your post as well as others. Here,you can also comment on others post by clicking on Leave a Reply option.
Step 6 After typing the comment, click on Post Comment option.
Using Offline Blog Editors
An offline blog editor is a very useful tool for bloggers because it lets you create blog posts without an Internet connection. So, instead of waiting for an online editor to load, your can just work offline. Offline editors let you create, edit and format your content before you upload it to your website. Some popular free offline blog editors are
- Windows Live Writer (For Windows)
- BlogDesk (For Windows)
- Qumana (For Windows and Mac)
- MarsEdit (ForMac) free only 3-0 days trial
Online Transaction and Online Shopping
Online transaction is a payment method in which the transfer of fund or money happens online over electronic fund transfer. Online shopping is the process of buying goods and services from merchants over the Internet. Books, clothing, household appliances, toys, hardware, software and health insurance are just some of hundreds of products consumers can buy from an online store.
Benefits of Online Shopping
Some benefits of online shopping are as follows:
- Online shopping is very convenient. You can get products at home.
- Online shopping’s websites provide millions of choices of product.
- They offer huge discount on goods and services.
- Online shops give us the opportunity to shop 24 × 7 hours and also reward us with cashback.
- Sending gifts to relatives and friends is easy by online shop.
Some Popular Online Websites
- Amazon and Flipkart An online shopping portal for buying consumer products.
- Nykaa An online shopping portal for beauty products.
- IRCTC An online portal for booking train tickets and seeing seat availability.
- RedBus An online portal for booking bus tickets.
- Myntra An online portal famous for branded clothing.
Transaction for Purchasing Goods at Flipkart
To purchase goods on Flipkart, follow the given steps:
Step 1 By web browser, open the Flipkart site.
Step2 Home page of Flipkart will appear as shown below
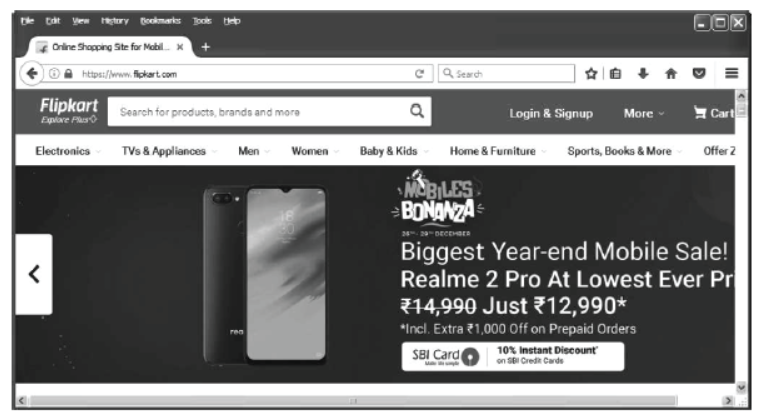
Step 3 Click on Login if you have an account on Flipkart otherwise click on Signup to register on Flipkart.
Step 4 A window will appear on screen with Enter Mobile Number field.
Step 5 Enter mobile number and click on CONTINUE. A window will be appear as shown below
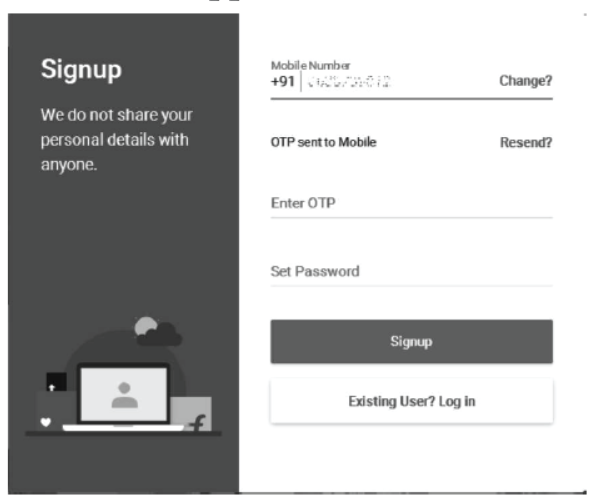
Step 6 You will received an OTP (One Time Password), enter this number and set password and then click on Sign up.
Step 7 Flipkart home screen will appear where different categories are given. You can select any category which you want.
Step 8 For example, select Sports, Books and More.
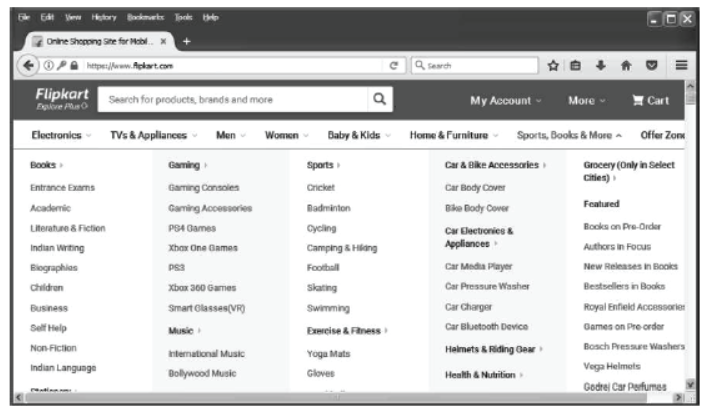
Step 9 The sub categories of Sports, Books and More will be display. In this category, select Books→ Indian Writing.
Step 10 Click on the item which you want to purchase and then click on Add to Cart.
Step 11 Now, click on My Cart and Cart window will appear as shown below.
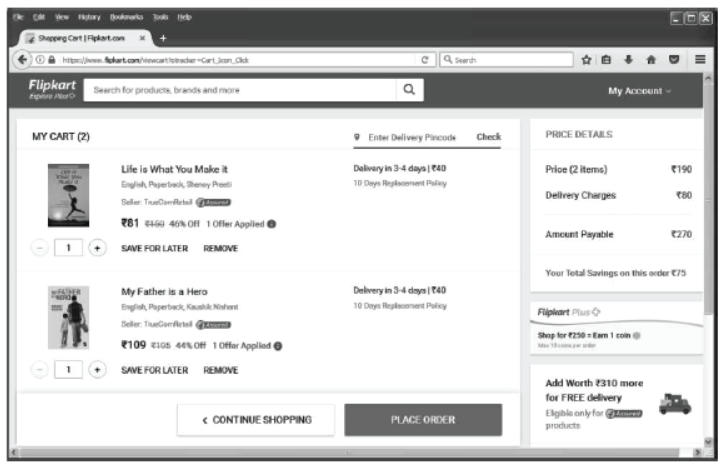
Step 12 Click on Place Order. A Delivery Address window will appear as shown below.
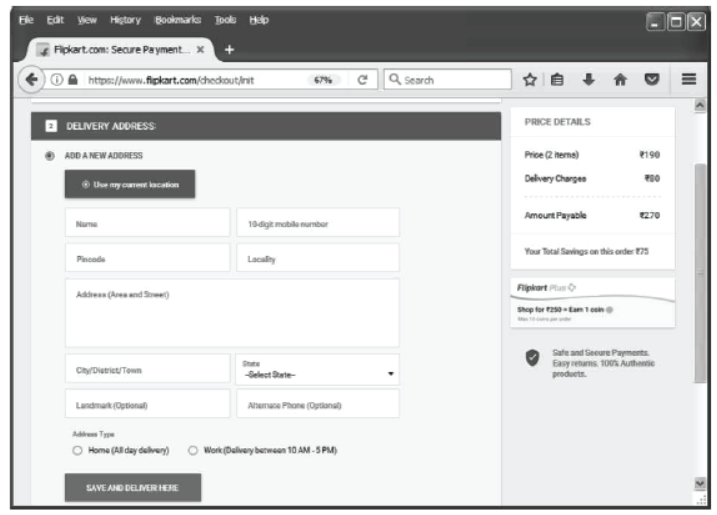
Step 13 Enter the details and click on Save And Deliver Here.
Step 14 The order summary page will appear and then click on Continue button.
Step 15 Payment Options window will appear as shown below. Here is the different payment methods. You can select any one of them. e.g. Cash on Delivery.
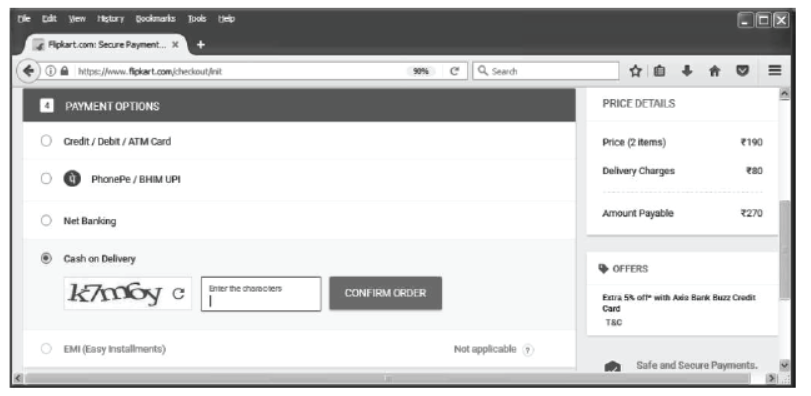
Step 16 Enter the characters in the given box and click on Confirm Order.
Step 17 After confirmation, a message will be received by you on registered mobile number.
Transaction for Booking Rail Tickets
An E–Ticket or electronic ticket is the digital ticket equivalent of a paper ticket. IRCTC (Indian Railway Catering and Tourism Corporation) is used to book and cancel rail tickets.
To book the ticket on IRCTC, follow the given steps
Step 1 Open the IRCTC site by www.irctc.co.in address. .
Step 2 Enter in From and To fields, class type and click on Find Trains option.
Step 3 Search the train and click on Check Availability and Fare to find the availability of train and book now.
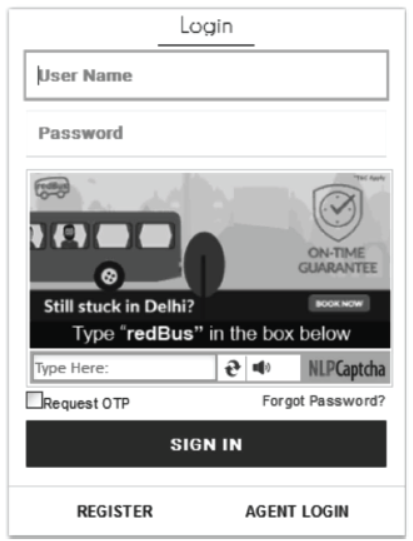
Step 4 The following page will display. If you have an account on IRCTC then enter login name and password otherwise click on REGISTER button.
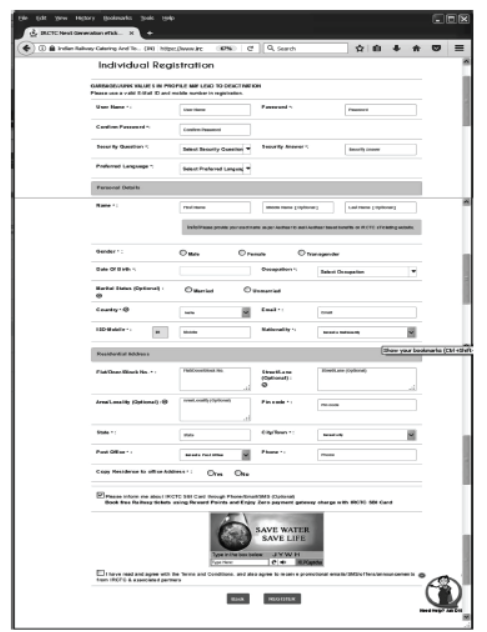
Step 5 Individual Registration page will appear, fill the details and click on REGISTER button.
Step 6 After this, a window will appear as shown below
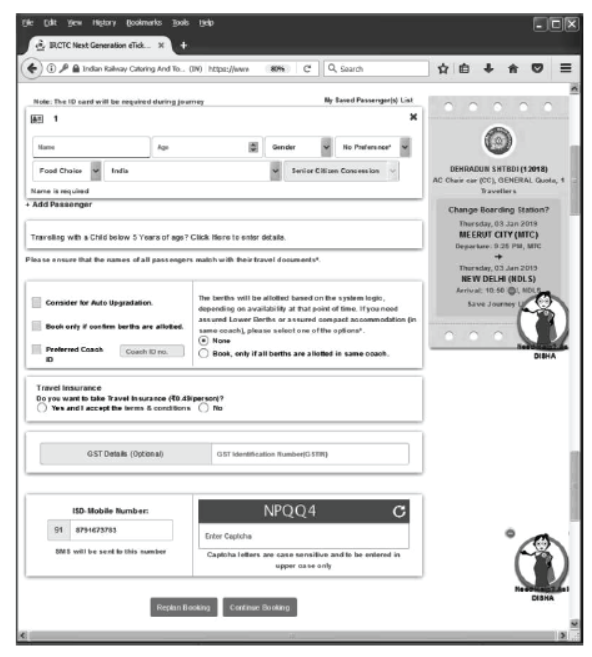
Step 7 Enter the required fields and click on Continue Booking.
Step 8 Travelling Passengers page will be appear as shown below.
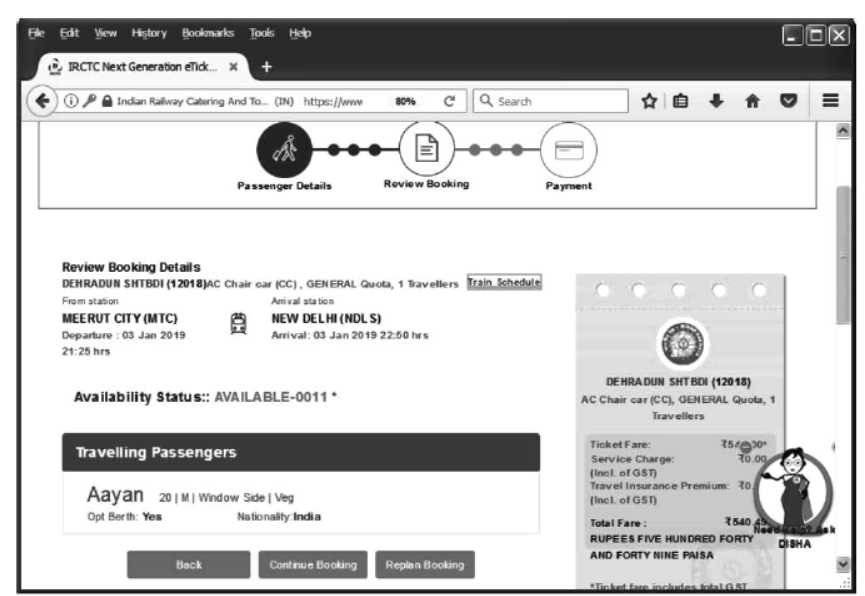
Step 9 Click on Continue Booking. Payment options page will be display on the screen. Select the appropriate option and enter details.
Step 10 Payment Page will be appear as shown below. Fill your bank details and click on Proceed button.
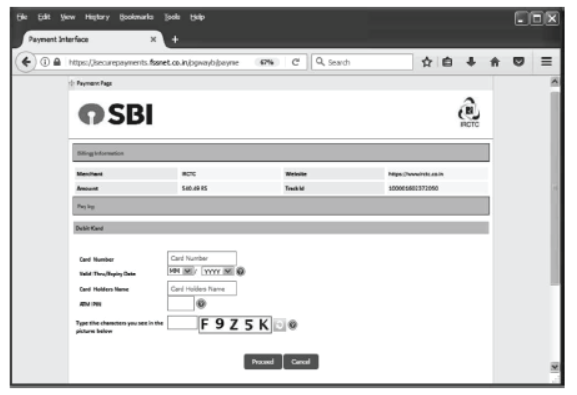
Step 11 E-ticket will be generated on screen as well as sent to your registered E-mail id.
Internet Security
It is a branch of computer security that deals specifically with Internet based threats. The Internet security prevents attacks targeted at browsers, networks, operating systems and other applications.
The main aim of Internet security is to set-up precise rules and regulations that can deflect attacks that arise from the Internet. Internet security relies on particular resources and criteria for safeguarding the data that is communicated or transferred online.
There are various best practices for Internet security, as follows
(i) Use Secure Password Your passwords are the most common way to prove your identity when using website, E-mail accounts and your computer itself. The use of strong password is therefore essential in order to protect your security and identity.
Do the following to choose the best password
- To create a strong password, simply choose three random words.
- You can use numbers, symbols and combination of uppercase and lowercase.
- Choose a password with atleast eight characters.
- Do not use your username, actual name or business name as password.
- Avoid to keep commonplace, dictionary word, your birthday date, etc.
- Avoid to use the word ‘Password’ and numerical sequence for password.
(ii) Install Anti-Virus Protection Only install an anti-virus program from a known and trusted source. Keep virus definitions, engines and software upto date to ensure your anti-virus program remains effective.
(iii) Keep Software upto Date Installing software updates for your operating system and programs in critical.Always install the latest security updates for your device.
- Turn on automatic updates for your operating system.
- Use web browser such as Google Chrome, etc., that receive frequent, automatic security updates.
- Make sure to keep browser plug-ins up to date.
(iv) Always Keep your Firewall Active Every computer is protected by a firewall. This firewall controls the flow of data over any network. Though firewall is the most secure feature in data protection. The firewalls provided mainly by the anti-virus developing companies are used.
(v) Always use Secure Network Connection Avoid doing crucial transaction over a public network. Any network other than your home or work network is an insecure network. Before using any connection other than trusted networks, always make sure that you secure the connection using appropriate VPN (Virtual Private Network) settings.
(vi) Backup your Data Backup on a regular basis, if you are a victim of a security incident, the only guaranteed way to repair your computer is to erase and re-install the system.
Various Cyber Threats
Phishing Phishing is an illegal practice in order to obtain personal and financial information, such as passwords, account IDs or credit card details and the attacker masquerading as a reputable personnel through the email or phone call. Phishing email messages are designed in such a way as to steal information. A person receives a message with a link, if the receiver clicks the link, the user is directed to a malicious website asking personal and financial details like credit card credentials, password, etc. If the user enter such personal and financial details, then that information will be taken away by the attacker and will be used for some illegal activities.Spoofing Spoofing, as it pertains to cybersecurity, is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money or spread malware. E-mail Spoofing E-mail spoofing is the creation of fake emails that seem legitimate. E-mail spoofing is used in both fraudulent schemes and targeted attacks against organizations. Cybercriminals use this technique to convince victims that a message came from a trusted sender and nudge them into performing a specific action, such as clicking a phishing link, transferring money, downloading a malicious file, etc. For added credibility, attackers can copy the design and style of a particular sender’s emails, stress the urgency of the task, and employ other social engineering techniques. SMTP (Simple Mail Transfer Protocol, the main email transmission protocol in TCP/IP networks) offers no protection against spoofing, so it is fairly easy to spoof the sender’s address.
Spamming These mails are also called junk mail that arrives in the ‘Spam’ mail box of an email account. These mails include advertising pamphlets and brochures. These mails are sent indiscriminately to multiple mailing lists, individuals or newsgroups in order to advertise their products and services. Cyberbullying Cyberbullying is a term referred to as bullying or harassing a person using electronic media like smart phones, tablets, computers through the use of communication tools like email, chatting session, text messages, posting rumors or embarrassing pictures on social media, etc. Due to the extensive use of internet, cyberbullying has become common, especially among teenagers.
Concept of Browser
A Web Browser is a software application that enables the users to access, retrieve and view the information and other resources on the Internet.
Some of the popular web browsers are Microsoft Internet Explorer, Microsoft Edge, Google Chrome, Mozilla Firefox,Opera and Netscape Navigator.
Types of Browsers
There are two types of browsers namely: graphical browsers and text-only browsers. Graphical browser Most commercial browsers are graphical browsers within which audio, video and pictures can be run or viewed. All the browsers named earlier are graphical. Text-only browser Lynx is an example of a text-only browser. It does not show up pictures, audio or video. In fact, it is meant for non-GUI systems. You may find it hard to believe but Lynx was once very popular.
Cookies
Cookies are small blocks of data created by a web server while a user is browsing a website and placed on the user's computer or other device by the user’s web browser.
Backup
Backup is a copy of computer data taken and stored elsewhere, so that it may be used to restore the original after a data loss event. Before you make changes to critical data always make a duplicate. Even if you just made a backup yesterday-make another.
Anti-virus Software
Anti-virus software is a utility software program that are installed on your computer to protect it from viruses. Anti-virus is also known as Anti-Malware and it is a computer program used to prevent, detect and remove malware.Some of the popular antivirus software are
Norton, Kaspersky, McAfree, AVG, Bit defender, Avast,Quick Heal, etc.
To use an anti-virus first install it on the computer. After installation, you can use it to scan your whole system.
Scanning Folder/Files
You can also scan folders and files. Steps to scan folder/file are as follows
Step 1 Select the folder/file for scanning.
Step 2 Right-click on the selected folder. A drop-down menu appears.
Step 3 Click on the Scan for Viruses option. The scanning will start.
Clearing data in browser
To clear the data in browser(Google Chrome), follow the given steps
Step 1 Open the web browser window.
Step 2 Click on the button. A menu appears.
Step 3 Click on History option. A submenu appears.
Step 4 Again, click on History option. A window appears.
Step 5 Click on the Clear browsing data option. All the data browsed till date will get deleted.
Maintain Workplace Safety
Information Technology needs team work to succeed. The environment in an IT firm is that people sitting together and working on their terminals. While work is important, there are other issues of working among people, related to disparity of salaries, lack of work culture and many such aspects. Sometimes the working conditions are not safe and calamities happen. These topics are rarely looked at during university computer courses but have their own place in the lives of software people. In this chapter, we will learn about the different methods though which we can maintain a good health while at workplace.
Listed below are some cases in which physical pain can happen. They are as follows
- Fire
- Falls and slips
- Electrical mishandling or calamity
- Cuts in flesh

Many of the topics brought up here are applicable to residential places of the people. We will stick to the office safety and health only here.
There are many possible causes for fire. Fire can be caused due to food being cooked, cigarettes being smoked, some garbage being burnt off, inadvertent flaring up of inflammable products, etc.
Some of the rules that companies have about fire safety are
- Do not smoke in the offices.
- Do not carry lighters or matches into the office.
- Do not use the elevator in times of fire in the building.
Always use the staircase for such emergencies.
- Get trained in the use of fire extinguishers.
While the other rules are obvious, the rule no. (d), has many sub-parts to it. There are different kinds of fire extinguishers. Some are meant for electrical fires, while others for chemical fires. In case of chemical fires, you may throw water from the extinguishers and it will extinguish the fire.

Occupational Safety and Health
It encompasses the social, mental and physical well-being of workers, that is the “whole” person.
Organizations can have become more effective, if they have safer and healthy workplaces. This is because:
- They have fewer days lost. Therefore, they have higher productivity.
- They can increase efficiency and quality. Because they have healthier workplace.
Electrical Safety
Employees should be trained in case of electrical fires and how to deal with such situations. In general, sand can be thrown into electrical fires. It should be known that water can never be used for electrical fires. Any other kind of fluid is also never used. There are many standards of wires and cabling that are conformant of fire safety and do not catch fire.
As the responsible person you must carry out and regularly review a fire risk assessment of the premises. This will identify what you need to do to prevent fire and keep people safe. You may carry out the assessment in the following manner.
- Identify the fire hazards.
- Identify people at risk.
- Evacuate, remove or reduce the risks.
- Record your findings, prepare an emergency plan and provide training.
- Review and update the fire risk assessment regularly.
As part of the fire risk assessment plan, you will need to consider
- Emergency routes and exits
- Fire detection and warning systems
- Fire-fighting equipments
- The removal or safe storage of dangerous substances
- An emergency fire evacuation plan
- The need to consider vulnerable people, e.g. the elderly, young children or those with disabilities
- Staff fire safety training

Fire Safety and Evacuation Plans
Some fire safety and evacuation plans are as follows
- A clear passageway to all escape routes.
- Clearly marked escape routes that are as short and direct as possible.
- Enough exits and routes for all people to escape.
- Emergency doors that open easily.
- A safe meeting point for staff.

Fire Detection and Warning System
You must have a fire detection and warning system. You may need different types of detectors, depending on the type of building and the work carries out in it.

Maintenance and Testing
You must carry out regular checks to make sure that:
- All fire alarms systems are working.
- The emergency lighting is working.
- You record any faults in systems and equipment.
- All escape routes are clear and the floor is in good condition.
- All fire escapes can be opened easily.
- Automatic fire doors close correctly.
- Fire exit signs are in the right place.

Fire safety is of the utmost importance in any building. As a business owner, you are responsible for ensuring that your workplace meets all required health and safety standards.
General Precautions in the Workplace
- Eliminate workplace hazards.
- Damaged electrical outlets, cords, cables, etc.
- Overloaded outlets and circuits.

- Fire exit obstacles.
- Keep workspace and equipment clean, dry and well-ventilated and especially clean of oil and dust.

Introduction to First Aid
At any moment, you or someone around you could experience an injury or illness. Using basic first aid, you may be able to stop a minor mishap from getting worse. In the case of a serious medical emergency, you may even save a life.

When you provide basic medical care to someone experiencing a sudden injury or illness, it is known as first aid.

In some cases, first aid consists of the initial support provided to someone in the middle of a medical emergency. This support might help them survive until professional help arrives. In other cases, first aid consists of the care provided to someone with a minor injury. For example, first aid is often all that’s needed to treat minor burns, cuts and insect stings.
First Aid Bandage
In many cases, you can use an adhesive bandage to cover minor cuts, scrapes or burns. To cover and protect larger wounds, you might need to apply a clean gauze pad or roller bandage.

First Aid for Burns
If you suspect that someone has a third-degree burn, call the hospital for ambulance. Seek professional medical care for any burns that:
- Cover a large area of skin
- Are located on the person’s face, groin, buttocks, hands or feet.
- Have been caught by contact with chemicals or electricity.

To treat a minor burn, run cool water over the affected area for up to 15 min. If that’s not possible, apply a cool compress to the area instead. Avoid applying ice to burned tissue, it can cause more damage.
Over-the-counter pain relievers can help relieve pain.
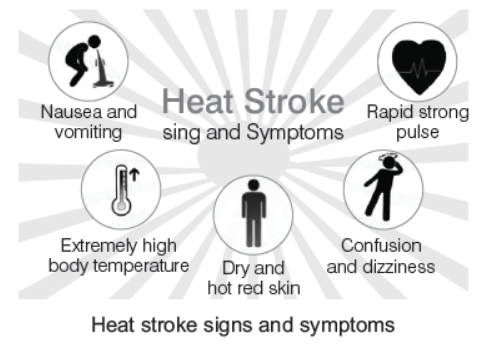
First Aid for Heat Stroke
When your body overheats, it can cause heat exhaustion. If left untreated, heat exhaustion can lead to heatstroke. This is a potentially life-threatening condition and medical emergency.
If someone is overheated, encourage them to rest in a cool location. Remove excess layers of clothing and try to cool their body down by doing the following:
- Cover them with a cool, damp sheet.
- Apply a cool, wet towel to the back of their neck.
- Sponge them with cool water.
Call the ambulance if they develop signs or symptoms of heatstroke, including any of the following:
- Nausea or vomiting - Mental confusion
- Fainting - Seizures
- A fever of 104 degree (40 degree C) or greater
Prevent Accidents and Emergencies
An accident at workplace is a physical or mental injury following an incident or exposure.
If you accidentally get injured in the workplace, the injury is not necessarily caused by your work. For example, You are getting up from a chair and suddenly got a strain in your neck.

How we examine an accident at work before we can assess if you have had an accident at work, we need the following
- Your employer’s signature that the incident or exposure occurred as well as any additional information.
- Information about your employer’s insurance company.
- A medical certificate describing the injury you have sustained due to the incident or exposure.
Types of Accidents in Workplace
There are many types of accidents that can occur in workplace. That’s why it’s so important for every small organisation to take the proper precautionary steps. Some common accidents that can occur in workplace are as follows
(i) Slips, Trips and Falls
One of the common accidents in workplace is slipping on wet floor or you likely encountered slippery tiled surfaces.
(ii) Muscle Strains
Another common type of accidents is strained muscles. This situation can occur with the person who lifts heavy weights at workplace.
(iii) Being Hit by Falling Objects
At the workplace, it may happen some objects may fall on you from shelves or out of the cupboard, causing some nasty injuries. Providing adequate storage cages and reminding employees of how to store items safely can go a long way to reducing this risk.

(iv) Repetitive Strain Injury
RSI is another problem that’s become increasingly commonplace at work over the years, though even now some employers don’t seem to take it entirely seriously.
(v) Crashes and Collisions
Accidents resulting in crash or impact injuries are also quite frequent at work. Whether they involve cars, lorries or even smaller vehicles such as forklift trucks, they can have seriously nasty consequences.
(vi) Cuts and Lacerations
All sorts of office implements can end up leaving their user nursing a painful cut. From power saws to paper trimmers, it’s easy to do yourself a mischief at work. The most common causes of these lacerations include poor training, inadequate safety procedures and failing to wear the proper protection. Bosses can help prevent such accidents by providing adequate safety equipment and putting the right procedures (including training) in place.

(vii) Inhaling Toxic Fumes
While most of us don’t work with hazardous chemicals, those of us who do may be at risk of skin or eye reactions as well as potentially more serious injuries, when exposed to them without protection.
Protective equipment such as safety goggles is indispensable in these situations, so employers must be sure to provide workers with the gear they need to avoid dangerous exposure.

(viii) Exposure to Loud Noise
You might think that industrial deafness is a thing of the past and went out with all those old heavy industries, but that’s not the case-not least because many industrial workers continue to be exposed to loud noises while at work. Industrial deafness can also result in major compensation payouts further along the line, so it’s very much in employers’ interest to nip this particular problem in the bud. Safety measures such as ear protection can do much to prevent it.

(ix) Walking into Objects
It’s probably safe to say we have all done this at some point. Maybe you are chatting absent-mindedly or maybe you are feeling a little under the weather, when you suddenly find yourself on the sharp end of a door, table, wall or cabinet. Needless to say, these injuries can sting a bit.
Luckily, many such accidents can be avoided by reminding employees to be vigilant and putting unnecessary hazards out of the way where people won’t walk into them.
(x) Fights at Work
These are not quite as rare as we might like to think. Simmering workplace tensions can bubble under for months or even years before spilling over into physical confrontation or alternatively one workmate can take another’s opinion on last weekend’s football the wrong way.
Fights in the workplace can, unsurprisingly, result in nasty injuries. Effective procedures for dealing with employee grievances can help reduce the risk of them coming to blows, though.
Handling Accidents
Good training, clear signage and access to the necessary safety equipment can all be a big help. Regular risk assessments are also a very good idea.
Your employer has a duty to protect you and tell you about health and safety issues that affect you. They must also report certain accidents and incidents, pay you sick pay and give you time off because of an accident at work should you need it.
On Hearing the Fire Alarm
- Close all the windows, doors and switch of non-essential services.
- Walk to the nearest assembly point.
- Follow the emergency signs.
- Escape routes should be lit by emergency lighting so that people can use them safely, if an emergency occurs.
- Do not re-enter the building until permission is given by the person in charge of the evacuation.
- If the fire is small, but only if you are trained to do so use fire extinguishers to attempt to put the fire out.
Employees Must Know
- The nearest means of escape.
- The nearest fire alarm call point.
- The nearest fire appliance and how to use it (Only if trained to do so).
- Their assembly points.
In the Event of a fire
- Do not panic.
- Maintain silence.
- Do not use the lift.
- Do not attempt to push,pull, pass others.
Workplace Emergency
Nobody expects an emergency or disaster but the simple truth is that these can strike anyone, anytime and anywhere. You and your employees could be forced to evacuate your company, when you least expect it.
The best way to protect yourself, your workers and your business is to expect the unexpected and develop a well-thought out emergency action plan to guide you, when immediate action is necessary.
A workplace emergency is an unforeseen situation that threatens your employees, customers or the public; disrupts or shuts down the workplace operations; or causes physical or environmental damage.
Emergency Action Plan
An emergency action plan covers designated actions employers and employees must take to ensure employee safety from fire and other emergencies. Putting together a comprehensive emergency action plan that deals with all types of issues specific to your worksite is not difficult.
You may find it beneficial to include your management team and employees in the process.
Developing an Evacuation Plan
A disorganised evacuation plan can result in confusion, injury and property damage. i.e. why when developing your emergency action plan it is important to determine the following
- Conditions under which an evacuation would be necessary.
- A clear chain of command and designation of the person in your business authorised to order an evacuation or shutdown. You may want to designate an “evacuation warden” to assist others in an evacuation and to account for personnel.
- Specific evacuation procedures, including routes and exits. Post these procedures, where they are easily accessible to all employees.

- Procedures for assisting people with disabilities or who do not speak English. Special attention must be given to evacuation procedures for persons with disabilities.
- Designation of what, if any, employees will continue or shut down critical operations during an evacuation.
These people must be capable of recognising, when toabandon the operation and evacuate themselves.
- A system for accounting for personnel following an evacuation. Consider employees’ transportation needs for community-wide evacuations.
Establishing Evacuation Routes and Exits
When preparing your emergency action plan, designate primary and secondary evacuation routes and exits. To the extent possible under the conditions, ensure that evacuation routes and emergency exits meet the following conditions:
- Clearly marked and well lit.
- Wide enough to accommodate the number of evacuating personnel.
- Unobstructed and clear of debris at all times.
- Unlikely to expose evacuating personnel to additional hazards.
Conducting Fire Exit Drills and Evacuations
To ensure that building occupants are prepared for an emergency evacuation, fire drills must be conducted periodically. A safe and orderly evacuation is more important than a quick evacuation.
Fire exit drills are only conducted by or under the direction of the Fire Safety Specialist for the Environmental Health,Safety and Risk Management office.
Emergency Procedure Maps
Emergency procedures diagrams are located within buildings throughout each campus. These diagrams provide floor plans showing the locations of emergency exits and emergency equipment (such as fire extinguishers) and maps for evacuation routes and emergency assembly areas.
Protect Health and Safety at Work Hazards
A hazard is any source of potential damage, harm or adverse health effects of the people at workplace. Hazard is a potential source of harm to the health of the worker or employee.
But, the exact meaning of the word hazard can be confusing,as often it is combined with the term risk.
Examples of a Hazard
Workplace hazards can come from a wide range of sources. General examples include any substance, material, process, practice, etc. that has the ability to cause harm or adverse health effect to a person or property.
| Workplace Hazard | Example of Hazard | Example of Harm Caused |
| Thing | Knife, Blade | Cut |
| Substance | Benzene | Leukaemia |
| Source of Energy | Electricity | Shock, electrocution |
| Condition | Wet floor | Slips, falls |
| Process | Welding | Metal fume fever |
| Behaviour | Bullying | Anxiety, fear, depression |
Let us specify the types of hazards are as follows:
- Biological hazards - Chemical hazards
- Ergonomic hazards - Physical hazards
- Psychosocial hazards - Safety hazards
Identification of hazards
General Evacuation Procedure during hazard By identifying hazards at your workplace, you will be better prepared to control or eliminate them and prevent accidents, injuries, property damage and downtime.Firstly, a key step in any safety protocol is to conduct a thorough hazard assessment of all work environments and equipments.
The following points must be kept in mind:
1. First aid boxes at various places in the office.
2. Trained first aiders-on all floors of a building.
3. Knowledge of the nearest casualty department or local hospital.
4. Access to call for an ambulance.
5. Ability to provide immediate assistance to casualties with illnesses or injuries caused by a specific hazard at work.
Health and Safety at Work
Your employer has to carry out a risk assessment and do what's needed to take care of the health and safety of employees and visitors. This includes deciding how many first aiders are needed and what kind of first aid equipment and facilities should be provided.
Healthy Living
You should maintain a healthy lifestyle to survive and sustain in the workplace.
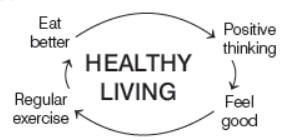
The various factors that should be taken into account to maintain a healthy living are as follows
- Watch your plate
- Watch your waist and weight
- Watch your steps
- Watch your stress level
- Watch your change
- Watch your tobacco and alcohol consumption
CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Multiple Choice Questions
Question. Which of the following is an application programthat is stored on a remote server and delivered over the Internet?
(a) Web application
(b) System application
(c) Internet application
(d) None of the above
Answer. A
Question. Computer connected with LAN
(a) work fast
(b) go online
(c) can E-mail
(d) can share information or peripheral devices
Answer. D
Question. A group of computers connected together with the help of cables within an office building is called
(a) PAN
(b) WAN
(c) MAN
(d) LAN
Answer. D
Question. Network formed between computers which exists across the continents is called
(a) LAN
(b) WAN
(c) MAN
(d) WLAN
Answer. B
Question. Digital information is converted into analog information by the modem at
(a) destination computer
(b) source computer
(c) Both (a) and (b)
(d) Neither (a) nor (b)
Answer. B
Question. Modulation and demodulation are performed by
(a) microwave
(b) satellite
(c) modem
(d) fibre optic
Answer. C
Question. A modemis connected between a telephone line and a
(a) computer
(b) serial port
(c) network
(d) communication adapter
Answer. A
Question. Which of the following is not a transmission medium?
(a) Telephone lines
(b) Co-axial cable
(c) Modem
(d) Microwave
Answer. C
Question. What can you do with the Internet?
(a) Exchange information with friends and colleagues
(b) Access pictures, sounds, video clips and other media elements
(c) Find diverse perspective on issues from a global audience
(d) Internet exchange information, access pictures,find diverse perspective on issue from a global audience
Answer. D
Question. The first network was
(a) ARPANET
(b) Internet
(c) NSFnet
(d) NET
Answer. A
Question. Which of these services will not be provided by a typical Internet Service Provider (ISP)?
(a) An E-mail address
(b) Modem
(c) A connection to the Internet
(d) Technical help
Answer. A
Question. To join the Internet, the computer has to be connected to a
(a) Internet architecture board
(b) Internet society
(c) Internet Service Provider
(d) None of the above
Answer. C
Question. Wireless broadband can be
(a) mobile
(b) fixed
(c) Both (a) and (b)
(d) None of the above
Answer. C
Question. Nick connects to the nternet at home using a laptop computer with a wireless connection. Nick is going to change use desktop computer using a 1 Gbps ethernet cable connection. Which of these should be the result of making the changes?
(a) Increased portability and decreased speed
(b) Decreased portability and increased speed
(c) Increased portability and increased speed
(d) Decreased portability and decreased speed
Answer. B
Question. ………… is a collection of web pages linked together in a random order.
(a) A website
(b) A web server
(c) A search engine
(d) A web browser
Answer. A
Question. Home page helps viewers to find out what they can find on the particular site? Home page is the
(a) first page of a website
(b) index page
(c) about page
(d) None of the above
Answer. A
Question. Which client software is used to request and display web pages?
(a) Web server
(b) Multimedia
(c) FTP
(d) Web browser
Answer. D
Question. .................. is an example of text-based browser which provides access to the Internet in the text-only mode.
(a) Mozilla Firefox
(b) Lynx
(c) Internet Explorer
(d) All of these
Answer. B
Question. Manoj has to set-up a network between his devices at home which included a smart phone, a laptop and a personal computer. What type of network he would be setting up for the same?
(a) PAN
(b) MAN
(c) WAN
(d) None of these
Answer. A
Question. Anila works in a Multi National Company (MNC) and needs to work online from home also. She requires fast Internet connection. Which type of Internet connection in your view would be best suited for her?
(a) Dialup
(b) Broadband
(c) Both are suitable
(d) None of these
Answer. B
Question. Sharvan Joshi is a student of Political Science and is a keen researcher of political issues related to various countries and states. He wants to share his research and his own opinions on these issues on day-to-day basis with everyone on World Wide Web (WWW). He is also interested in collecting views of others to enhance his research and knowledge related to his area of interest. He belongs to a middle class family and cannot afford his own website. Also being a non- technical person, he cannot create a dynamic website to deal with day-to-day inputs. Suggest an easy way for Sharvan to achieve the same.
(a) He should develop an E-mail id
(b) He should develop his research online
(c) He should develop a blog
(d) He should use instant messaging app
Answer. C
Question. What type of hazard are caused by stress violence at workplace?
(a) Chemical hazard
(b) Safety hazard
(c) Psychological hazard
(d) None of these
Answer. C
Question. Which type of hazard can cause skin irritation, illness or breathing problems?
(a) Chemical hazard
(b) Biological hazard
(c) Slipping hazard
(d) None of the above
Answer. A
Question. Do not use the elevator in times of fire in the building. Always use…………… for such emergencies.
(a) office space
(b) washroom
(c) staircase
(d) None of these
Answer. C
Question. If you have a safer and healthy workplace, there will be fewer days lost and will have higher
(a) Employee satisfaction
(b) Productivity
(c) Stress levels
(d) None of the above
Answer. B
Question. You should conduct regular fire drills in order to
(a) Eliminate workplace hazards
(b) Prepare for emergencies
(c) Carry out the risk assessment
(d) None of the above
Answer. A
Question. Which of the following falls in the category of workplace emergency?
(a) Earthquake
(b) Tornadoes
(c) Both (a) and (b)
(d) None of these
Answer. C
Question. What is the full form of RSI?
(a) Repetitive Strain Injury
(b) Rational Strain Injury
(c) Repetitive Stress Injury
(d) Risk Strain Injury
Answer. A
Question. A web page is located using a
(a) Universal Record Linking
(b) Uniform Resource Locator
(c) Universal Record Locator
(d) Uniformly Reachable Links
Answer. B
Question. Instant messaging service accepts instant messages from
(a) external sites
(b) internal sites
(c) Both (a) and (b)
(d) None of these
Answer. A
Question. Which of the following is an application based instant messaging software?
(a) Google Talk
(b) eBuddy
(c) Meebo
(d) MSN Web Messenger
Answer. A
Question. A blog consists of
(a) images
(b) text
(c) links
(d) All of these
Answer. D
Question. ................ is the act of posting content on a blog.
(a) Edublog
(b) Posting
(c) Blogging
(d) Blogger
Answer. C
Question. Which of the following offers a blog service?
(a) Drupal
(b) Joomla
(c) WordPress.com
(d) All of these
Answer. D
Question. Qumana is an offline blog editor which is used for ........... operating system(s).
(a) Windows
(b) Mac
(c) Both (a) and (b)
(d) None of these
Answer. C
Question. Which of the following websites is used for booking train tickets?
(a) Nykaa
(b) IRCTC
(c) RedBus
(d) Myntra
Answer. B
Direction Read the case and answer the following questions.
1. A WAN spans a large physical distance. The Internet is the largest WAN, spanning the Earth. A WAN is a geographically-dispersed collection of Lans. A network device called a router connects LANs to a WAN. In IP networking, the router maintains both a LAN address and a WAN address. They are owned by multiple organisations.
Question. What is the full form of WAN?
(a) World Area Network
(b) Wide Area Nest
(c) Wide Area Network
(d) Wide Access Network
Answer. C
Question. How much physical distance a WAN spans to?
(a) Large distance
(b) Small distance
(c) Within the same building
(d) Within the office/home
Answer. A
Question. ………… is the largest WAN, spanning the Earth.
(a) Technology
(b) Internet
(c) Distance
(d) Router
Answer. B
Question. A ………… connects LANs to a WAN.
(a) Wire
(b) Pen drive
(c) CD
(d) Router
Answer. D
Question. How many organisation(s) own WAN?
(a) Single organisation
(b) Multiple organisations
(c) Two organisations
(d) None of these
Answer. B
2. World Wide Web (WWW ) or simply web is a set of programs, standards and protocols that allows the multimedia and hypertext files to be created, displayed and linked on the Internet. The World Wide Web was invented in 1989. It became publicly available on Internet for the first time. The Internet is the physical network of computers all over the world. The World Wide Web is a virtual network of websites connected by hyperlinks (or “links”). Websites are stored on servers on the internet, so the World Wide Web is a part of the Internet.
Question. WWW stands for ………… .
(a) World Wide Web
(b) Word Wide Web
(c) World Way Web
(d) Web World Wide
Answer. A
Question.World Wide Web (WWW) is a set of programs, standards and protocols that allows the multimedia and hypertext files to be created, displayed and linked on the ………… .
(a) ARPNET
(b) CSNET
(c) Internet
(d) CERN
Answer. C
Question. Which of the following is/are stored on servers of Internet?
(a) WWW
(b) Websites
(c) Internet
(d) Links
Answer. B
Question. ARPANET stands for ………… .
(a) Advanced Research Projects Agency NETwork
(b) Advanced Research Product Agency NETwork
(c) Advanced Research Process Agency NETwork
(d) Advanced Research Plan Agency NETwork
Answer. A
Question. In which year was WWW invented?
(a) 1988
(b) 1989
(c) 1990
(d) 1992
Answer. B
CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Short Answer Type Questions
Question. Name the term defined by given below statement:
‘‘A group of computers connected to each other by a link.’’
Answer. Computer network is defined as a group of computers connected to each other by a link that allows sharing of resources and information.
Question. What is the definition of networking? [CBSE Textbook]
Answer. A computer networking is the practice for exchanging information/services between two or more computers together for the purpose of sharing data.
Question. What are the main types of computer networks?
Answer. Following are the three main types of computer networks, based upon the geographical area as follows:
(i) Local Area Network (LAN)
(ii) Metropolitan Area Network (MAN)
(iii) Wide Area Network (WAN)
Question. What is the main purpose of switch?
Answer. A switch is a hardware device which is used to connect devices or segment of network with smaller subsets of LAN segments.
Question. Identify the following devices.
(i) A device that is used to connect different types of networks. It performs the necessary translation, so that the connected networks can communicate properly.
(ii) A device that converts data from digital bit stream into an analog signal and vice-versa.
Answer. (i) Router (ii) Modem
Question. What is the advantage of mesh topology?
Answer. In mesh topology, each node is connected to more than one node, so that it provides alternative route. In case, if the host is either down or busy.
Question. Give the names of models of computer networking.
Answer. There are mainly two models of computer networking as follows:
(i) Peer-to-Peer network (ii) Client-server network
Question. How many techniques are used for transmitting data across network?
Answer. There are three techniques used for transmitting data across network : circuit switching, packet switching and message switching.
Question. Write two advantages of using Internet.
Answer. Advantages of using Internet are as follows:
(i) It is used for communication, entertainment, searching information and for providing many types of services.
(ii) It provides the facility of E-mail.
Question. Name any five DSL broadband service providers in India.
Answer. BSNL, Airtel, Reliance, MTNL and Tata Indicom are the five DSL broadband service providers in India.
Question. Write the name of any two Internet Service Provider (ISP) in India.
Answer. MTNL and Airtel are the two Internet Service Provider (ISP) in India.
Question. Name any two ways of wireless connections of Internet. Ramya wants to connect all the computers of her office wirelessly in order to avoid uncoordinated cables. Which wireless technology would be best suitable for her office?
Answer. Wi-Fi and WiMax are the two ways of wireless connections of Internet. Wi-Fi technology would be best suitable for her office to avoid cabling. Because, it allows high speed Internet connections without the use of cables or wires.
Question. Write the full form of following terms.
(i) WiMAX
(ii) BPL
Answer. (i) WiMAX Worldwide Interoperability for Microwave Access.
(ii) BPL Broadband over Power Line
Question. What can a user do with WWW? Name any two major services provided by Internet.
Answer. Using WWW (World Wide Web), a user can download files, listen to music, view video files and jump to other documents or websites by using hypertext links. E-mail and WWW are the two major services provided by Internet.
Question. Mr. Lal owns a factory which manufactures automobile spare parts. Suggest him the advantages of having a web page for his factory.
Answer. The web page provides the information to the clients about his factory of spare parts. Moreover, he can receive the order on the Internet from the clients using the web page.
Question. Name two web browsers of Internet.
Answer. Internet Explorer and Google Chrome are the two web browsers of Internet.
Question. What is URL? Can we use URL to access a web page? How?
Answer. URL means Uniform Resource Locator. It is a unique address of a web page on the Internet. It specifies the Internet address of a file stored on a host computer connected to the Internet. Yes, as a location on a web server, which is called a website and each website has a unique address known as URL. So, an URL can be used to access a web page.
Question. Identify web addresses and E-mail addresses from the following.
(i) www.scrapbook.com
(ii) aba@scrapbook.com
(iii) www.countrywide.co.in
(iv) 123@hotshot.co.in
Answer. Key features of an Instant Messaging are:
(i) and (iii) are web addresses.
(ii) and (iv) are E-mail addresses.
Question. Write any two key features of an Instant Messaging (IM).
Answer. Key features of an Instant Messaging are :
(i) Video calling
(ii) Language translation
Question. List any five application based instant messaging software.
Answer. Whatsapp, Viber, Skype, WeChat, Google Talk
Question. Who is blogger? List any five websites that provide blog service.
Answer. A person who writes a blog or a weblog is known as blogger. Blogging is the act of posting content on a blog.
Any five websites that provide blog service listed below
(i) Joomla
(ii) Blogger
(iii) Word Press.com
(iv) Tumblr
(v) Drupal
Question. Explain the purpose of a blog.
Answer. The main purpose of blog is to convey messages about events, announcements, need, review, etc. Blogs are usually managed using a web browser and this requires active internet connection.
Question. Laluma Chakradhar wants a broadband connection to access her mails and stay informed about the latest happening in the field of Biotechnology. Can you suggest two Internet Service Providers (ISPs) of India to be approached for the same?
Answer. BSNL and Airtel
Question. Explain the concept ‘Watch Your waist and weight; to maintain a healthy body at workplace’.
Answer. The explanation of the concept ‘Watch Your waist and weight; to maintain a healthy body at workplace’ is
(i) Encourage the use of weighing scales, measuring tapes and devices to monitor individual physical fitness.
(ii) Place weighing scales, measurement tapes and body mass index charts in strategic locations.
Question. What are the advantages of having safer and healthy workplace?
Answer. The advantages of having safer and healthy workplaces are as follows:
(i) They have fewer days lost, therefore they have higher productivity.
(ii) They can increase efficiency and quality, because they have healthier workplace.
Question. What are physical hazards?
Answer. Physical hazards can be any factors within the environment that can harm the body without necessarily touching it. It can be caused by radiation (microwave, radio wave), pressure extremes (high pressure or vacuum), constant loud noise, high exposure to sunlight/ultraviolet rays,temperature extremes (hot and cold), etc.
Question. What are slipping and tripping hazards?
Answer. Slipping hazards are causes through spills or trips such as cords running across the floor or water spilled on the floor. Tripping hazards are caused through falls such as working from heights, including ladders, scaffolds, roofs, etc.
Question. How does water and foam fire extinguisher work?
Answer. Water and foam fire extinguishers extinguish the fire by taking the heat element away from the fire. Water extinguishers are for class A fires. Class A fires involve ordinary combustile materials, such as cloth, wood, paper, rubber and many plastics.
Question. How does carbon dioxide fire extinguisher work?
Answer. Carbon Dioxide fire extinguishers extinguish fire by taking away the oxygen element of the fire triangle and also be removing the heat with a very cold discharge. Carbon dioxide can be used on Class B and C fires. They are usually ineffective on Class A fires.
Question. How does wet chemical fire extinguisher work?
Answer. Wet chemical is a new agent that extinguishes the fire by removing the heat of the fire triangle and prevents re-ignition by creating a barrier between the oxygen and fuel elements.
Wet chemical of Class K extinguishers were developed for modem, high efficiency deep fat fryers in commercial cooking operations. Some may also be used on Class. A fires in commercial kitchens.
Question. Write down any three points of differences between LAN, MAN and WAN.
Answer. Three major points of differences among LAN, MAN and WAN are as follows
(i) In terms of geographical area WAN covers the area across the continents, MAN covers area within a city while LAN covers area within a building.
(ii) In terms of distance The approximate distance covered by WAN is unlimited, of MAN is upto 160 km while that of LAN is upto 5 km.
(iii) In terms of speed The speed with which the data travels in case of WAN is 10 to 38.4 Kbps, 183 to 7.2 Mbps, while that of MAN is 11 to 100 Mbps and of LAN is 11 to 54 Mbps.
Question. Explain the LAN and WAN.
Answer. A Local Area Network (LAN) is a computer network covering a small geographical area like a home, office or small group of buildings such as buildings in a school. Computers connected to a LAN can share information and peripheral equipments.
A Wide Area Network (WAN) is used to connect LANs and other types of network together, so that users and computers in one location can communicate with users and computers in other locations.
Question. What is the use of repeater in a network?
Answer. In a network, repeater receives a weak signal coming from a source and amplifies it to its original strength and then again forwards it to the destination. Basically, repeaters are used in a network so that a signal can travel longer distance.
Question. When the computer network uses telephone lines as communication channel, then MODEM is used as a data communication device. Now, explain the working of MODEM.
Answer. MODEM performs the task of modulation at sender's site and demodulation at the receiver’s site. Basically, our computer generates data in the form of digital signals which need to be forwarded to the receiver through telephone lines. Since, telephone lines can carry only analog signals. So, digital signals need to be converted to analog signals at sender’s site this is called modulation. At receiver’s site, again analog signals should be converted back to the original digital signals, then this is called demodulation.
Question. Difference between circuit switching and packet switching.
Answer. Differences between circuit switching and packet switching are as follows
| Circuit Switching | Packet Switching |
| Initially designed for voice communication. | Initially designed for data transmission. |
| Inflexible, because once a path is set all parts of a transmission follows the same path. | Flexible, because a route is created for each packet to travel to the destination. |
| It is connection oriented. | It is connectionless. |
Question. Elucidate the following terms.
(i) PAN (ii) WiMAX (iii) Satellite
Answer.
(i) PAN It stands for Personal Area Network. It is a computer network used for communication among computer and different technological devices close to it.
(ii) WiMAX It stands for Worldwide Interoperability for Microwave Access. It is a wireless transmission of data using a variety of transmission modes.
(iii) Satellite which are orbiting around the Earth, provide necessary links for telephone and television service.
Question. Why do we use Instant Messaging?
Answer. Instant messaging is a set of communication technologies used for text based communication between two or more participants over the Internet or other types of networks. Many instant messaging services offer video calling features, Voice over Internet Protocol (VoIP) and web conferencing services. Web conferencing services can integrate both video calling and instant messaging abilities.
Question. How can you prepare for emergencies?
Answer. To prepare for emergencies, follow the given guidelines
(i) Follow workspace protocol and guidelines to ensure safety and health; know and understand rules and procedures concerning fire emergencies.
(ii) Ensure that smoke alarms and sprinkler systems are installed, working properly and are not blocked.
(iii) Conduct regular fire drills.
Question. Explain any three rules that companies follows in terms of fire safety.
Answer. Any four rules that companies follows in terms of fire safety are as follows
(i) All fire alarms systems are working.
(ii) All fire escapes can be opened easily.
(iii) Automatic fire doors close correctly.
Question. Explain three conditions following which evacuation is done.
Answer. Any three conditions following which evacuation is done are
- In the event of a fire, an immediate evacuation is to be followed by the employees.
- In case of tornadoes, earthquakes, floods or explosions, the type of building can be a major factor in taking decision to follow the evacuation plan.
- If a designated person within your workplace, under some circumstances had taken the decision to evacuate or shut down operations.
Question. What are biological hazards?
Answer. Biological hazards are caused by bacteria, viruses, insects, plants, birds, animals and humans, etc. It includes exposure to harm or disease associated with working with animals, people or infectious plant materials. Workplaces like schools, day care, colleges, hospitals, laboratories or various outdoor establishments are more exposed to such type of biological hazards.
Question. How does dry chemical fire extinguisher work?
Answer. Dry chemical fire extinguishers extinguish the fire primarily by interrupting the chemical reaction of the fire triangle. Today’s most widely used type of fire extinguisher is the multipurpose dry chemical that is effective on Class A, B and C fires. This agent also works by creating a barrier between the oxygen element and the fuel element on Class A fires.
Ordinary dry chemical is for Class B and C fires only. It is important to use the correct extinguisher for the type of fuel. Using the incorrect agent can allow the fire to re-ignite after apparently being extinguished successfully.
CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Long Answer Type Questions
Question. Why is Internet called ‘Network of Networks’?
Answer. Internet is called ‘Network of Networks’ because it is global network of computers that are linked together by cables and telephone lines making communication possible among them. It can be defined as a global network over a million of smaller heterogeneous computer networks.
The network which consists of thousands of networks spanning the entire globe is known as Internet. The Internet is a world wide collection of networked computers, which are able to exchange information with each other very quickly. Mostly people use the Internet in two ways, E-mail and World Wide Web. In Internet, most computers are not connected directly, they are connected to smaller networks, which in turn are connected through gateways to the Internet backbone. A gateway is a device that connects dissimilar networks. A backbone is central interconnecting structure - that connects one or more networks.
Question. Give an example of E-mail address and explain each part of it.
Answer. The example of an E-mail address is abc@gmail.com. The format of E-mail address is username@hostname or domain name. So, as per the above example of E-mail address. abc is the username and gmail.com is the name of hosting server or host (domain) name. Thus, we can say that, E-mail address has two parts separated by ‘@’ symbol.
(i) Username On the left side of separator @ is the user name. A user name cannot have blanks.
(ii) Domain Name for the Host Server The portion to the right of @ identifies the server or host network that services your E-mail. It is also known as E-mail server.
Question. What do you mean by Instant Messaging? Also, explain one Instant Messaging software.
Answer. Instant Messaging (IM), formof text-based communication in which two persons participate in a single conversation over their computers or mobile devices within an Internet based chatroom.
Various softwares provide instant messaging services as Whatsapp, Google Talk, Skype, Meebo, eBuddy, etc. Google Talk It is an instant messaging and VoIP service developed by Google. This client lets you to log in to the service to chat and hold video-conferences with your friends from the windows desktop. Google Talk is more than just a regular chat, you can also make free PC to PC VoIP calls and even leave voice messages like an answering machine. If your contacts are also using the Google Hangouts client, you can send files too. Google Hangouts was integrated into G-mail where users could send instant messages to other G-mail users. As it worked within a browser, the Google Talk client did not need to be downloaded to send instant messages to G-mail users.
Question. What is switching? Explain the different types of switching techniques.
Answer. Switching is a technique which is used in large networks. It is a hardware or software device which creates a connection between one or more computers. Switching is basically of three types which are as follows
(i) Circuit Switching In this type of technique, an end-to-end path is created before sending the data (dedicated channel, i.e. Circuit). The data is transferred using physical connection which is set upto between sender and receiver.
(ii) Message Switching Message switching is based on the transfer of block of messages from sender to receiver. Firstly, the address of destination is attached in a message. When a sender has a block of data to be sent, it is stored in the first switching station and then forwarded later. Each block of message is received entirely, checked for errors and then retransmitted.
There is no need for physical connection between packet which has header that contains source and destination addresses information acknowledgement and error bits.
(iii) Packet Switching In packet-based networks, the message gets broken into small data packets. These packets are sent out from the computer and they travel around the network seeking out the most efficient route to travel as circuits become available.
Question. What is a topology? Explain the types of topologies.
Answer. Topology refers to the topology of a network. Topology refers to the way in which a network is laid out physically. Topology is the geometric representation of the relationship of all the nodes to the one another. There are mainly four types of topologies as discussed below(i) Mesh Topology In mesh topology, each computer is
connected to every other computer to provide an alternate path for transferring data.
(ii) Star Topology In a star topology, each computer is connected to a centrally located device called hub.
(iii) Bus Topology In a bus topology, one long cable acts as a backbone to link all the computers in a network.
(iv) Ring Topology In a ring topology, each computer is connected with the two computers on either side of it.
Question. What are the preventive measures to avoid cyberbullying?
Answer. Preventive measures to be taken to avoid cyberbullying are given as
(i) Check your privacy settings in social media like Facebook, so that your friends can only view your profile and posts.
(ii) You should think twice while posting any message, as internet is public.
(iii) Always keep your personal information like name, address, phone number, school name, credit card or debit card credentials, password, etc., private.
Question. What are some examples of workplace hazards?
Answer. Some examples of workplace hazards are as follows:
(i) Damaged electrical outlets, cords, cables, etc.
(ii) Overloaded outlets and circuits.
(iii) Combustible substances in unsecured locations,
(including excessive trash and recycling) - keep these far from electrical equipment.
(iv) Fire exit obstacles.
Keep workspace and equipment clean, dry and well-ventilated and especially clean of oil and dust.
Question. What is the first aid you should apply for burns?
Answer. If you suspect that someone has a third-degree bum, call the hospital for ambulance. Seek professional medical care for any bums that
(i) Cover a large area of skin.
(ii) Are located on the person’s face, groin, buttocks, hands or feet.
(iii) Have been caught by contact with chemicals or electricity.
To treat a minor burn, run cool water over the affected area for up to 15 min. If that’s not possible, apply a cool compress to the area instead. Avoid applying ice to burned tissue, it can cause more damage.
Over-the-counter pain relievers can help relieve pain.
Question. What is a workplace emergency?
Answer. A workplace emergency is an unforeseen situation that threatens your employees, customers or the public;disrupts or shuts down the workplace operations; or causes physical or environmental damage.
Emergencies may be natural or manmade and include the following
- Floods - Hurricanes
- Fires - Tornadoes
- Toxic gas releases
- Chemical spills
- Radiological accidents
- Explosions
- Civil disturbances
- Workplace violence resulting in bodily harm and trauma
Question. Write any five precautions that are to be taken at the workplace.
Answer. Any five precautions that are to be taken of at the workplace are as follows:
(i) Take responsibility and clean up, if you made a mess.
(ii) Clean and organise your workspace.
(iii) Ensure a clear and easy route to emergency exits and equipment.
(iv) Be alert and awake on the job.
(v) Be attentive at all times to your work surroundings.
Question. Explain the concept ‘Watch Your Plate’ to maintain a healthy body at workplace.
Answer. The explanation of the concept ‘Watch Your Plate’ to maintain a healthy body at workplace is
(i) Promote consumption of a variety of foods and awareness regarding their serving sizes.
(ii) Encourage conscious calorie reduction.
(iii) Make available fresh vegetables and fruits in the cafeteria.
(iv) Make clean water the default drink in the workplace and at meetings and discourage sugar-sweetened beverages.
(v) Discourage consumption of foods high in salt, sugar and saturated and transfats.
Question. Explain some of the ways to remove workplace hazards.
Answer. Some of the ways to eliminate workplace hazards are as follows
(i) Remove damaged electrical outlets, cords, cables, etc.
(ii) Check overloaded outlets and circuits.
(iii) Combustible substances in unsecured locations,(including excessive trash and recycling) - keep these far from electrical equipment.
(iv) Clear all fire exit obstacles.
(v) Keep workspace and equipment clean, dry and well-ventilated and especially clean of oil and dust.
(vi) Follow workspace protocol and guidelines to ensure safety and health; know and understand rules and procedures concerning fire emergencies.
(vii) Ensure that smoke alarms and sprinkler systems are installed, working properly and are not blocked.
(viii) Conduct regular fire drills.
Question. Explain some of the actions that are used in the event of fire.
Answer. Some actions that should be used in the event of a fire are as follows:
(i) Close all the windows, doors and switch of non-essential services.
(ii) Walk to the nearest assembly point.
(iii) Follow the emergency signs.
(iv) Escape routes should be lit by emergency lighting so that people can use them safely if an emergency occurs.
(v) Don’t re-enter the building until permission is given by the person in charge of the evacuation.
(vi) If the fire is small, but only if you are trained to do so use fire extinguishers to attempt to put the fire out.
Question. Explain any five precautions at workplace.
Answer. Any five precautions at workplace are as follows:
(i) First aid boxes at various places in the office.
(ii) Trained first aiders - on all floors of a building.
(iii) Knowledge of the nearest casualty department or local hospital.
(iv) Access to call for an ambulance.
(v) Ability to provide immediate assistance to casualties with illnesses or injuries caused by a specific hazard at work.
Question. Explain how to apply roller bandage to a wound.
Answer. To apply a roller bandage to a wound, follow these steps:
(i) Hold the injured area steady.
(ii) Gently but firmly wrap the bandage around the injured limb or body part, covering the wound.
(iii) Fasten the bandage with sticky tape or safety pins.
(iv) The bandage should be wrapped firmly enough to stay put, but not so tightly that it cuts off blood flow.
To check the circulation in a bandaged limb, pinch one of the person’s fingernails or toenails until the color drains from the nail. If color do not return within two seconds of letting go, the bandage is too tight and needs to be adjusted.
Question. Explain any five moves that an employee can do on hearing the fire alarm.
Answer. On hearing the fire alarm, the employees should
(i) Close all the windows, doors and switch of non-essential services.
(ii) Walk to the nearest assembly point.
(iii) Follow the emergency signs.
(iv) Escape routes should be lit by emergency lighting, so that people can use them safely if an emergency occurs.
(v) Don’t re-enter the building until permission is given by the person in charge of the evacuation.
Question. How does keeping a watch at the stress level can help to sustain in the workplace?
Answer. (i) Introduce stress consultation and counselling services for staff.
(ii) Create a physical space for reflection and thinking.
(iii) Create a system to reinforce a healthy, positive and balanced workplace.
(iv) Promote de-stressing (relaxation) exercise, e.g. yoga, tai-chi, deep breathing, meditation, etc.
(v) Create time and space for recreational activities at work.
(vi) Build social support groups.
Short Answer Type Questions :
Question. When the computer network uses telephone lines as communication channel, then MODEM is used as a data communication device. Now, explain the working of MODEM.
Answer. MODEM performs the task of modulation at sender’s site and demodulation at the receiver’s site. Basically, our computer generates data in the form of digital signals which need to be forwarded to the receiver through telephone lines. Since, telephone lines can carry only analog signals. So, digital signals need to be converted to analog signals at sender’s site this is called modulation. At receiver’s site, again analog signals should be converted back to the original digital signals, then this is called demodulation.
Question. How does carbon dioxide fire extinguisher work?
Answer. Carbon Dioxide fire extinguishers extinguish fire by taking away the oxygen element of the fire triangle and also be removing the heat with a very cold discharge. Carbon dioxide can be used on Class B and C fires. They are usually ineffective on Class A fires.
Question. How can you prepare for emergencies?
Answer. To prepare for emergencies, follow the given guidelines
(i) Follow workspace protocol and guidelines to ensure safety and health; know and understand rules and procedures concerning fire emergencies.
(ii) Ensure that smoke alarms and sprinkler systems are installed, working properly and are not blocked.
(iii) Conduct regular fire drills.
Question. Who is blogger? List any five websites that provide blog service.
Answer. A person who writes a blog or a weblog is known as blogger. Blogging is the act of posting content on a blog.
Any five websites that provide blog service listed below
(i) Joomla
(ii) Blogger
(iii) Word Press.com
(iv) Tumblr
(v) Drupal
Question. Name any five DSL broadband service providers in India.
Answer. BSNL, Airtel, Reliance, MTNL and Tata Indicom are the five DSL broadband service providers in India.
Question. How many techniques are used for transmitting data across network?
Answer. There are three techniques used for transmitting data across network : circuit switching, packet switching and message switching.
Question. Write any two key features of an Instant Messaging (IM).
Answer. Key features of an Instant Messaging are :
(i) Video calling
(ii) Language translation
Question. What are the main types of computer networks?
Answer. Following are the three main types of computer networks, based upon the geographical area as follows:
(i) Local Area Network (LAN)
(ii) Metropolitan Area Network (MAN)
(iii) Wide Area Network (WAN)
Question. Name two web browsers of Internet.
Answer. Internet Explorer and Google Chrome are the two web browsers of Internet.
Question. Name any two ways of wireless connections of Internet. Ramya wants to connect all the computers of her office wirelessly in order to avoid uncoordinated cables. Which wireless technology would be best suitable for her office?
Answer. Wi-Fi and WiMax are the two ways of wireless connections of Internet. Wi-Fi technology would be best suitable for her office to avoid cabling. Because, it allows high speed Internet connections without the use of cables or wires.
Question. What are slipping and tripping hazards?
Answer. Slipping hazards are causes through spills or trips such as cords running across the floor or water spilled on the floor. Tripping hazards are caused through falls such as working from heights, including ladders, scaffolds, roofs, etc.
Question. List any five application based instant messaging software.
Answer. Whatsapp, Viber, Skype, WeChat, Google Talk
Question. Mr. Lal owns a factory which manufactures automobile spare parts. Suggest him the advantages of having a web page for his factory.
Answer. The web page provides the information to the clients about his factory of spare parts. Moreover, he can receive the order on the Internet from the clients using the web page.
Question. What is the main purpose of switch?
Answer. A switch is a hardware device which is used to connect devices or segment of network with smaller subsets of LAN segments.
Question. What is the use of repeater in a network?
Answer. In a network, repeater receives a weak signal coming from a source and amplifies it to its original strength and then again forwards it to the destination. Basically, repeaters are used in a network so that a signal can travel longer distance.
Question. How does dry chemical fire extinguisher work?
Answer. Dry chemical fire extinguishers extinguish the fire primarily by interrupting the chemical reaction of the fire triangle. Today’s most widely used type of fire extinguisher is the multipurpose dry chemical that is effective on Class A, B and C fires. This agent also works by creating a barrier between the oxygen element and the fuel element on Class A fires.
Ordinary dry chemical is for Class B and C fires only. It is important to use the correct extinguisher for the type of fuel. Using the incorrect agent can allow the fire to re-ignite after apparently being extinguished successfully.
Question. Explain the LAN and WAN.
Answer. A Local Area Network (LAN) is a computer network covering a small geographical area like a home, office or small group of buildings such as buildings in a school. Computers connected to a LAN can share information and peripheral equipments.
A Wide Area Network (WAN) is used to connect LANs and other types of network together, so that users and computers in one location can communicate with users and computers in other locations.
Question. What are physical hazards?
Answer. Physical hazards can be any factors within the environment that can harm the body without necessarily touching it. It can be caused by radiation (microwave, radio wave), pressure extremes (high pressure or vacuum), constant loud noise, high exposure to sunlight/ultraviolet rays,temperature extremes (hot and cold), etc.
Question. Explain three conditions following which evacuation is done.
Answer. Any three conditions following which evacuation is done are
- In the event of a fire, an immediate evacuation is to be followed by the employees.
- In case of tornadoes, earthquakes, floods or explosions, the type of building can be a major factor in taking decision to follow the evacuation plan.
- If a designated person within your workplace, under some circumstances had taken the decision to evacuate or shut down operations.
Question. Explain the concept ‘Watch Your waist and weight; to maintain a healthy body at workplace’.
Answer. The explanation of the concept ‘Watch Your waist and weight; to maintain a healthy body at workplace’ is
(i) Encourage the use of weighing scales, measuring tapes and devices to monitor individual physical fitness.
(ii) Place weighing scales, measurement tapes and body mass index charts in strategic locations.
Question. Write the full form of following terms.
(i) WiMAX
(ii) BPL
Answer. (i) WiMAX Worldwide Interoperability for Microwave Access.
(ii) BPL Broadband over Power Line
Question. Write two advantages of using Internet.
Answer. Advantages of using Internet are as follows:
(i) It is used for communication, entertainment, searching information and for providing many types of services.
(ii) It provides the facility of E-mail.
Question. Explain the purpose of a blog.
Answer. The main purpose of blog is to convey messages about events, announcements, need, review, etc. Blogs are usually managed using a web browser and this requires active internet connection.
Question. What are the advantages of having safer and healthy workplace?
Answer. The advantages of having safer and healthy workplaces are as follows:
(i) They have fewer days lost, therefore they have higher productivity.
(ii) They can increase efficiency and quality, because they have healthier workplace.
Question. Explain any three rules that companies follows in terms of fire safety.
Answer. Any four rules that companies follows in terms of fire safety are as follows
(i) All fire alarms systems are working.
(ii) All fire escapes can be opened easily.
(iii) Automatic fire doors close correctly.
Question. Laluma Chakradhar wants a broadband connection to access her mails and stay informed about the latest happening in the field of Biotechnology. Can you suggest two Internet Service Providers (ISPs) of India to be approached for the same?
Answer. BSNL and Airtel
Question. Elucidate the following terms.
(i) PAN
(ii) WiMAX
(iii) Satellite
Answer. (i) PAN It stands for Personal Area Network. It is a computer network used for communication among computer and different technological devices close to it.
(ii) WiMAX It stands for Worldwide Interoperability for Microwave Access. It is a wireless transmission of data using a variety of transmission modes.
(iii) Satellite which are orbiting around the Earth, rovide necessary links for telephone and television service.
Question. Give the names of models of computer networking.
Answer. There are mainly two models of computer networking as follows:
(i) Peer-to-Peer network
(ii) Client-server network
Question. How does water and foam fire extinguisher work?
Answer. Water and foam fire extinguishers extinguish the fire by taking the heat element away from the fire. Water extinguishers are for class A fires. Class A fires involve ordinary combustile materials, such as cloth, wood, paper, rubber and many plastics.
Question. What can a user do with WWW? Name any two major services provided by Internet.
Answer. Using WWW (World Wide Web), a user can download files, listen to music, view video files and jump to other documents or websites by using hypertext links. E-mail and WWW are the two major services provided by Internet.
Question. Name the term defined by given below statement: ‘‘A group of computers connected to each other by a ink.’’
Answer. Computer network is defined as a group of computers connected to each other by a link that allows sharing of resources and information.
Question. Identify the following devices.
(i) A device that is used to connect different types of networks. It performs the necessary translation, so that the connected networks can communicate properly.
(ii) A device that converts data from digital bit stream into an analog signal and vice-versa.
Answer. (i) Router
(ii) Modem
Question. What are biological hazards?
Answer. Biological hazards are caused by bacteria, viruses, insects, plants, birds, animals and humans, etc. It includes exposure to harm or disease associated with working with animals, people or infectious plant materials. Workplaces like schools, day care, colleges, hospitals, laboratories or various outdoor establishments are more exposed to such type of biological hazards.
Question. What is the advantage of mesh topology?
Answer. In mesh topology, each node is connected to more than one node, so that it provides alternative route. In case, if the host is either down or busy.
Question. Why do we use Instant Messaging?
Answer. Instant messaging is a set of communication technologies used for text based communication between two or more participants over the Internet or other types of networks. Many instant messaging services offer video calling features, Voice over Internet Protocol (VoIP) and web conferencing services. Web conferencing services can integrate both video calling and instant messaging abilities.
Question. How does wet chemical fire extinguisher work?
Answer. Wet chemical is a new agent that extinguishes the fire by removing the heat of the fire triangle and prevents e-ignition by creating a barrier between the oxygen and fuel elements.
Wet chemical of Class K extinguishers were developed for modem, high efficiency deep fat fryers in commercial cooking operations. Some may also be used on Class. A fires in commercial kitchens.
Question. What is the definition of networking?
Answer. A computer networking is the practice for exchanging information/services between two or more computers together for the purpose of sharing data.
Question. Write down any three points of differences between LAN, MAN and WAN.
Answer. Three major points of differences among LAN, MAN and WAN are as follows
(i) In terms of geographical area WAN covers the area across the continents, MAN covers area within a city while LAN covers area within a building.
(ii) In terms of distance The approximate distance covered by WAN is unlimited, of MAN is upto 160 km while that of LAN is upto 5 km.
(iii) In terms of speed The speed with which the data travels in case of WAN is 10 to 38.4 Kbps, 183 to 7.2 Mbps, while that of MAN is 11 to 100 Mbps and of LAN is 11 to 54 Mbps.
Question. What is URL? Can we use URL to access a web page? How?
Answer. URL means Uniform Resource Locator. It is a unique address of a web page on the Internet. It specifies the Internet address of a file stored on a host computer connected to the Internet. Yes, as a location on a web server, which is called a website and each website has a unique address known as URL. So, an URL can be used to access a web page.
Question. Write the name of any two Internet Service Provider (ISP) in India.
Answer. MTNL and Airtel are the two Internet Service Provider (ISP) in India.
Question. Identify web addresses and E-mail addresses from the following.
(i) www.scrapbook.com
(ii) aba@scrapbook.com
(iii) www.countrywide.co.in
(iv) 123@hotshot.co.in
Answer. Key features of an Instant Messaging are:
(i) and
(ii) and
(iii) are web addresses.
(iv) are E-mail addresses.
Long Answer Type Questions :
Question. What is a topology? Explain the types of topologies.
Answer. Topology refers to the topology of a network. Topology refers to the way in which a network is laid out physically. Topology is the geometric representation of the relationship of all the nodes to the one another. There are mainly four types of topologies as discussed below
(i) Mesh Topology In mesh topology, each computer is connected to every other computer to provide an alternate path for transferring data.
(ii) Star Topology In a star topology, each computer is connected to a centrally located device called hub.
(iii) Bus Topology In a bus topology, one long cable acts as a backbone to link all the computers in a network.
(iv) Ring Topology In a ring topology, each computer is connected with the two computers on either side of it.
Question. Explain any five precautions at workplace.
Answer. Any five precautions at workplace are as follows:
(i) First aid boxes at various places in the office.
(ii) Trained first aiders – on all floors of a building.
(iii) Knowledge of the nearest casualty department or local hospital.
(iv) Access to call for an ambulance.
(v) Ability to provide immediate assistance to casualties with illnesses or injuries caused by a specific hazard at work.
Question. Explain the concept ‘Watch Your Plate’ to maintain a healthy body at workplace.
Answer. The explanation of the concept ‘Watch Your Plate’ to maintain a healthy body at workplace is
(i) Promote consumption of a variety of foods and awareness regarding their serving sizes.
(ii) Encourage conscious calorie reduction.
(iii) Make available fresh vegetables and fruits in the cafeteria.
(iv) Make clean water the default drink in the workplace and at meetings and discourage sugar-sweetened beverages.
(v) Discourage consumption of foods high in salt, sugar and saturated and transfats.
Question. Explain some of the actions that are used in the event of fire.
Answer. Some actions that should be used in the event of a fire are as follows:
(i) Close all the windows, doors and switch of non-essential services.
(ii) Walk to the nearest assembly point.
(iii) Follow the emergency signs.
(iv) Escape routes should be lit by emergency lighting so that people can use them safely if an emergency occurs.
(v) Don’t re-enter the building until permission is given by the person in charge of the evacuation.
(vi) If the fire is small, but only if you are trained to do so use fire extinguishers to attempt to put the fire out.
Question. Give an example of E-mail address and explain each part of it.
Answer. The example of an E-mail address is abc@gmail.com. The format of E-mail address is username@-hostname or domain name. So, as per the above example of E-mail address. abc is the username and gmail.com is the name of hosting server or host (domain) name. Thus, we can say that, E-mail address has two parts separated by ‘@’ symbol.
(i) Username On the left side of separator @ is the user name. A user name cannot have blanks.
(ii) Domain Name for the Host Server The portion to the right of @ identifies the server or host network that services your E-mail. It is also known as E-mail server.
Question. Write any five precautions that are to be taken at the workplace.
Answer. Any five precautions that are to be taken of at the workplace are as follows:
(i) Take responsibility and clean up, if you made a mess.
(ii) Clean and organise your workspace.
(iii) Ensure a clear and easy route to emergency exits and equipment.
(iv) Be alert and awake on the job.
(v) Be attentive at all times to your work surroundings.
Question. What are some examples of workplace hazards?
Answer. Some examples of workplace hazards are as follows:
(i) Damaged electrical outlets, cords, cables, etc.
(ii) Overloaded outlets and circuits.
(iii) Combustible substances in unsecured locations, (including excessive trash and recycling) – keep these far from electrical equipment.
(iv) Fire exit obstacles.
Keep workspace and equipment clean, dry and well-ventilated and especially clean of oil and dust.
Question. What is switching? Explain the different types of switching techniques.
Answer. Switching is a technique which is used in large networks. It is a hardware or software device which creates a connection between one or more computers.
Switching is basically of three types which are as follows
(i) Circuit Switching In this type of technique, an end-to-end path is created before sending the data (dedicated channel, i.e. Circuit). The data is transferred using physical connection which is set upto between sender and receiver.
(ii) Message Switching Message switching is based on the transfer of block of messages from sender to receiver. Firstly, the address of destination is attached in a message. When a sender has a block of data to be sent, it is stored in the first switching station and then forwarded later. Each block of message is received entirely, checked for errors and then retransmitted.
There is no need for physical connection between packet which has header that contains source and destination addresses information acknowledgement and error bits.
(iii) Packet Switching In packet-based networks, the message gets broken into small data packets. These packets are sent out from the computer and they travel around the network seeking out the most efficient route to travel as circuits become available.
Question. What are the preventive measures to avoid cyberbullying?
Answer. Preventive measures to be taken to avoid cyberbullying are given as
(i) Check your privacy settings in social media like Facebook, so that your friends can only view your profile and posts.
(ii) You should think twice while posting any message, as internet is public.
(iii) Always keep your personal information like name, address, phone number, school name, credit card or debit card credentials, password, etc., private.
Question. How does keeping a watch at the stress level can help to sustain in the workplace?
Answer. (i) Introduce stress consultation and counselling services for staff.
(ii) Create a physical space for reflection and thinking.
(iii) Create a system to reinforce a healthy, positive and balanced workplace.
(iv) Promote de-stressing (relaxation) exercise, e.g. yoga, tai-chi, deep breathing, meditation, etc.
(v) Create time and space for recreational activities at work.
(vi) Build social support groups.
Question. Explain how to apply roller bandage to a wound.
Answer. To apply a roller bandage to a wound, follow these steps:
(i) Hold the injured area steady.
(ii) Gently but firmly wrap the bandage around the injured limb or body part, covering the wound.
(iii) Fasten the bandage with sticky tape or safety pins.
(iv) The bandage should be wrapped firmly enough to stay put, but not so tightly that it cuts off blood flow.
To check the circulation in a bandaged limb, pinch one of the person’s fingernails or toenails until the color drains from the nail. If color do not return within two seconds of letting go, the bandage is too tight and needs to be adjusted.
Question. What do you mean by Instant Messaging? Also, explain one Instant Messaging software.
Answer. Instant Messaging (IM), formof text-based communication in which two persons participate in a single conversation over their computers or mobile devices within an Internet based chatroom.
Various softwares provide instant messaging services as Whatsapp, Google Talk, Skype, Meebo, eBuddy, etc. Google Talk It is an instant messaging and VoIP service developed by Google. This client lets you to log in to the service to chat and hold video-conferences with your friends from the windows desktop. Google Talk is more than just a regular chat, you can also make free PC to PC VoIP calls and even leave voice messages like an answering machine. If your contacts are also using the Google Hangouts client, you can send files too.
Google Hangouts was integrated into G-mail where users could send instant messages to other G-mail users. As it worked within a browser, the Google Talk client did not need to be downloaded to send instant messages to G-mail users.
Question. Why is Internet called ‘Network of Networks’?
Answer. Internet is called ‘Network of Networks’ because it is global network of computers that are linked together by cables and telephone lines making communication possible among them. It can be defined as a global network over a million of smaller heterogeneous computer networks.
The network which consists of thousands of networks spanning the entire globe is known as Internet. The Internet is a world wide collection of networked computers, which are able to exchange information with each other very quickly. Mostly people use the Internet in two ways, E-mail and World Wide Web. In Internet, most computers are not connected directly, they are connected to smaller networks, which in turn are connected through gateways to the Internet backbone. A gateway is a device that connects dissimilar networks. A backbone is central interconnecting structure – that connects one or more networks.
Question. Explain some of the ways to remove workplace hazards.
Answer. Some of the ways to eliminate workplace hazards are as follows
(i) Remove damaged electrical outlets, cords, cables, etc.
(ii) Check overloaded outlets and circuits.
(iii) Combustible substances in unsecured locations, (including excessive trash and recycling) – keep these far from electrical equipment.
(iv) Clear all fire exit obstacles.
(v) Keep workspace and equipment clean, dry and well-ventilated and especially clean of oil and dust.
(vi) Follow workspace protocol and guidelines to ensure safety and health; know and understand rules and procedures concerning fire emergencies.
(vii) Ensure that smoke alarms and sprinkler systems are installed, working properly and are not blocked.
(viii) Conduct regular fire drills.
Question. Explain any five moves that an employee can do on hearing the fire alarm.
Answer. On hearing the fire alarm, the employees should
(i) Close all the windows, doors and switch of non-essential services.
(ii) Walk to the nearest assembly point.
(iii) Follow the emergency signs.
(iv) Escape routes should be lit by emergency lighting, so that people can use them safely if an emergency occurs.
(v) Don’t re-enter the building until permission is given by the person in charge of the evacuation.
Question. What is the first aid you should apply for burns?
Answer. If you suspect that someone has a third-degree bum, call the hospital for ambulance. Seek professional medical care for any bums that
(i) Cover a large area of skin.
(ii) Are located on the person’s face, groin, buttocks, hands or feet.
(iii) Have been caught by contact with chemicals or electricity.
To treat a minor burn, run cool water over the affected area for up to 15 min. If that’s not possible, apply a cool compress to the area instead. Avoid applying ice to burned tissue, it can cause more damage.
Over-the-counter pain relievers can help relieve pain.
Question. What is a workplace emergency?
Answer. A workplace emergency is an unforeseen situation that threatens your employees, customers or the public;disrupts or shuts down the workplace operations; or causes physical or environmental damage.
Emergencies may be natural or manmade and include the following
- Floods
- Hurricanes
- Fires
- Tornadoes
- Toxic gas releases
- Chemical spills
- Radiological accidents
- Explosions
- Civil disturbances
- Workplace violence resulting in bodily harm and trauma
| CBSE Class 10 Computer Science Animation In 3D Max Notes |
| CBSE Class 10 Computer Science Basics Of Information Technology Notes |
| CBSE Class 10 Computer Science Chapter 1 Entrepreneurial Skills-II Notes |
| CBSE Class 10 Computer Science Chapter 2 Green Skills-II Notes |
| CBSE Class 10 Computer Science Chapter 3 Database Management System Notes |
| CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes |
| CBSE Class 10 Computer Science Customizing And Embedding Multimedia Notes |
| CBSE Class 10 Computer Science Digital Documentation Advanced |
| CBSE Class 10 Computer Science Electronic Spreadsheet Advanced |
| CBSE Class 10 Computer Science ICT Skills II |
| CBSE Class 10 Computer Science Information Processing Tool Notes |
| CBSE Class 10 Computer Science Operating Web Based Application Notes |
| CBSE Class 10 Computer Science Review Of Autodesk 3D Max Notes |
| CBSE Class 10 Computer Science Self Management Skills II |
| CBSE Class 10 Computer Science Societal Impacts Of It Notes |
| CBSE Class 10 Computer Science Web Scripting Using JavaScript Notes |
Important Practice Resources for Free Printable Worksheets PDF
CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes
Students can use these Revision Notes for Chapter 4 Web Applications and Security to quickly understand all the main concepts. This study material has been prepared as per the latest CBSE syllabus for Class 10. Our teachers always suggest that Class 10 students read these notes regularly as they are focused on the most important topics that usually appear in school tests and final exams.
NCERT Based Chapter 4 Web Applications and Security Summary
Our expert team has used the official NCERT book for Class 10 Computer Science to design these notes. These are the notes that definitely you for your current academic year. After reading the chapter summary, you should also refer to our NCERT solutions for Class 10. Always compare your understanding with our teacher prepared answers as they will help you build a very strong base in Computer Science.
Chapter 4 Web Applications and Security Complete Revision and Practice
To prepare very well for y our exams, students should also solve the MCQ questions and practice worksheets provided on this page. These extra solved questions will help you to check if you have understood all the concepts of Chapter 4 Web Applications and Security. All study material on studiestoday.com is free and updated according to the latest Computer Science exam patterns. Using these revision notes daily will help you feel more confident and get better marks in your exams.
You can download the teacher prepared revision notes for CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes from StudiesToday.com. These notes are designed as per 2025-26 academic session to help Class 10 students get the best study material for Computer Science.
Yes, our CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes include 50% competency-based questions with focus on core logic, keyword definitions, and the practical application of Computer Science principles which is important for getting more marks in 2026 CBSE exams.
Yes, our CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes provide a detailed, topic wise breakdown of the chapter. Fundamental definitions, complex numerical formulas and all topics of CBSE syllabus in Class 10 is covered.
These notes for Computer Science are organized into bullet points and easy-to-read charts. By using CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes, Class 10 students fast revise formulas, key definitions before the exams.
No, all study resources on StudiesToday, including CBSE Class 10 Computer Science Chapter 4 Web Applications and Security Notes, are available for immediate free download. Class 10 Computer Science study material is available in PDF and can be downloaded on mobile.

