Get the most accurate NCERT Solutions for Class 10 Computers Societal Impacts of IT here. Updated for the 2025-26 academic session, these solutions are based on the latest NCERT textbooks for Class 10 Computers. Our expert-created answers for Class 10 Computers are available for free download in PDF format.
Detailed Societal Impacts of IT NCERT Solutions for Class 10 Computers
For Class 10 students, solving NCERT textbook questions is the most effective way to build a strong conceptual foundation. Our Class 10 Computers solutions follow a detailed, step-by-step approach to ensure you understand the logic behind every answer. Practicing these Societal Impacts of IT solutions will improve your exam performance.
Class 10 Computers Societal Impacts of IT NCERT Solutions PDF
Very Short Answer Type Questions [1 Mark each]
Question. Define virus.
Answer: A virus is a harmful program, which on entering a computer, starts creating copies of itself. It then attacks by corrupting the executable files and folders saved on the computer.
Question. List the different types of computer viruses.
Answer:
1. File system viruses
2. Boot sector viruses
3. Macro viruses
Question. Name some forms of virus attacks.
Answer: Worms, Trojan horse, Computer Virus etc.
Question. Give some examples of computer worms.
Answer: MS-Blaster, Mellisa worm, SQL Slammer worm are the common examples of worms.
Question. Explain denial of service attack.
Answer: A denial of service attack is a type of attack that consumes all the resources of a computer.
Question. What is used to identify, prevent and take action against malicious programs, such as viruses and worms, by deactivating or deleting them?
Answer: Antivirus is used to identify, prevent and take action against malicious programs such as viruses and worms, by deactivating or deleting them.
Question. Describe hacking.
Answer: Hacking is the practice of modifying the features of a system, in order to accomplish a goal outside of the creator’s original purpose.
Question. What is the meaning of backup?
Answer: Backup is a process of making an extra copy of the data on a computer and storing it in a different location on the computer or in an external device.
Question. What are the types of data backup?
Answer: There are two types of data backup:
1. Full backup
2. Differential backup
Question. Can you backup the files while your computer is running?
Answer: Yes, we can safely backup open files and programs while they are running.
Question. What is encryption of data?
Answer: Encryption refers to scrambling of data in some encoded format so that it may be transmitted over networks.
Question. A digital signature is issued by which organisation?
Answer: A digital signature is«an electronic file that is issued by a Certification Authority. (CA).
Question. Name two other means of online security measures.
Answer: Digital signature and Digital certificate
Question. Which security provision is used to ensure data integrity and authentication?
Answer: A digital signature helps the user to ensure data integrity and authentication.
Question. Give any two shortcomings of online purchase.
Answer:
1. Cannot see the product in reality before a purchase.
2. You do not receive the product immediately, there is always some delay.
Short Answer Type Questions
Question. How does a virus affect your computer?
Answer: Virus is a software used to infect a computer. After virus code is written, it is buried within an essential programmed. Once the programmed is executed, the virus code is activated and attack copies itself to other programs.
Question. Give three guidelines to prevent the virus attack.
Answer: Three guidelines to prevent the virus attack are as follows:
1. Avoid the temptation to open unexpected E-mail attachments and downloads from unreliable sources. Resist the urge to double click everything in your mailbox. If you
get an unexpected file attachment, send an enquiry E-mail to its sender. Ask him about the nature and function of the file attachment.
2. In stable reliable antivirus, scanning software and download its updates regularly.
3. Scan files downloaded from the Internet or other external sources.
Question. If your computer attacked by a trojan horse virus, what damage it may cause?
Answer: If your computer attacked by a trojan horse virus, it can:
1. Steal passwords
2. Copy sensitive data
3. Carry out any other harmful operations etc.
Question. Write minimum three ways by which a virus can spread to other systems.
Answer: Three ways by which a virus can spread to other systems are as follows:
1. When an infected file is copied through network.
2. When virus file is downloaded from Internet.
3. When infected file is copied from floppy disk, USB, DVD etc.
Question. Write any two tips to avoid spams.
Answer: You can use the following guidelines to avoid spam, they are as follows:
1. Keep your E-mail address private.
2. Using appropriate filters to find and alter you about spam.
Question. What are the primary interest of online attackers in spyware?
Answer: Primary interest of online attackers in spyware is using it to steal personal information for financial crimes such as carding and identity theft or to sell that information to someone else who then executes more traditional financial crimes.
Question. What does an antivirus software do?
or
What does an antivirus software do? Explain in brief with any two points.
Answer:
1. Antivirus software is a computer program that detects, prevents and takes action to disarm or remove malicious software programs, such as viruses and worms.
2. Displays health of your computer system.
Question. What precaution you should take before copying file from an external storage media?
Answer: Precaution should be taken to run an antivirus program before copying any file from floppy disk, USB, DVD etc. Also, we have to run antivirus program weekly to scan all the drives in the system.
Question. List some commonly available antivirus programs.
Answer: Some of the commonly available antivirus programs in the market are as follows:
1. Symantec Norton antivirus
2. AVG antivirus
3. McAfee scan
4. Quick Heal
Question. Define information security.
Answer: Information security is all about protecting and preserving information. It’s all about protecting and preserving the confidentiality, integrity, authenticity, availability and reliability of information.
Question. Differentiate between full backup and differential backup.
Answer: Differences between full backup and differential backup are as follows:
Full backup Differential backup
A complete backup of everything The backup software looks at which files have
that you want to backup. changed, since you last did a full backup.
Restoration is fast, since you only Faster to create than a full backup.
need one set of backup data.
Question. Write differences between online backup and offline backup.
Answer: Differences between online backup and offline backup are as follows:
Online backup Offline backup
You don’t have direct control over The data is totally in your control.
your data.
If you have a fire, flood, or theft, your If you have a fire or flood, your backup
backup is offsite so you don’t have to might be damaged alongwith your
worry about it. computer.
Question. List two advantages of online backup.
Answer: Two advantages of online backup are as follows:
1. By having your data stored on a remote hard drive, you run little as there is no risk of losing your data as a result of fire, theft or any other disaster.
2. No hardware is needed to maintain or repair the backup.
Question. Can firewalls detect virus?
Answer: Firewalls do not screen computer viruses.
As the location of firewalls is a good place for scanning, some firewalls has plug-in virus scanning module.
And some programs scan virus at a point either before or after a firewall.
Question. Mention three societal impacts of IT.
Answer: The societal impacts of IT are as follows:
1. Opportunities for people with disabilities through artificial intelligence.
2. Quality of life improvements due to E-Commerce over Internet.
3. Crime fighting and other benefits.
Question. Why should we frequently take backup of our data?
Answer: We frequently take backup of our data because
1. The hard drive of our computer may fail.
2. The data on our computer may get corrupted for a variety of reasons.
3. Data loss due to fire, natural disasters etc.
Question. Differentiate between digital certificate and digital signature.
Answer: Differentiate between digital certificate and digital signature are as follows:
Digital certificate Digital signature
Digital certificates are typically A digital signature is a mechanism that is used
used in Websites to increase their to verify that a particular digital document or
trustworthiness to its users. a message is authentic.
Digital certificates are used, the With digital signatures, the receiver can verify
assurance is mainly dependent on that the information is not modified.
the assurance provided by the CA.
Question. Name one specific software/tool for each of the following categories:
1. Antivirus software
2. Data recovery tool
3. Online backup tool
Answer:
1. Antivirus software – Quick Heal
2. Data recovery tool – NTFS Reader
3. Online backup tool – Dropbox
Question. Give the three terms related to the following:
1. Attacks
2. Backup
3. Security software
Answer:
1. Attacks Trojan horse, Worm, Denial of Service.
2. Backup Online backup, Full backup, Differential backup.
3. Security software Digital signature, Firewall, Antivirus.
Question. Name four data backup devices/medium.
Answer: Four storage media on which data backup may be taken are as follows:
1. DVD (Digital Versatile Disk)
2. External hard disk
3. USB flash drive
4. Memory stick
Long Answer Type Questions
Question. What are the common symptoms of a virus attack?
Answer: Symptoms of Computer Viruses Attack
The list of symptoms of computer viruses attack, which indicate that your system is infected with a computer viruses are as follows:
1. Odd messages are displaying on the screen.
2. Some files are missing.
3. System runs slower.
4. PC (Personal Computer) crash or restart again and again.
5. Drives are not accessible.
6. Antivirus software will not run or installed.
7. Unexpected sound or music plays.
8. The mouse pointer changes its graphic.
9. Receive strange E-mails containing odd attachments or viruses.
10. PC starts performing functions like opening or closing windows, running programs on its own.
Question. What are the various measures that should be taken to prevent spyware from overtaking your system?
Answer: Preventions of Spyware
Due to the seriousness of spyware and the harm, it can affect your system and personal information, it is highly recommended you to take the given measures to prevent spyware from overtaking your system:
- Download and install anti-spyware software: Most antivirus applications are effective in identifying different types of malware, including spyware, but may not detect all spyware variants. Once you install the anti-spyware software on your computer, you must keep your anti-spyware application updated to keep up with the latest forms of spyware.
- Be cautious when Web surfing: The best defense against spyware is not to download it in the first place. Spyware is often installed on your computer when you visit an infected or malicious Website.
Therefore, you should exercise caution with links to Websites from unknown sources. In addition, you should only download programs from trustful Websites. When downloading a specific program, ensure that you are not downloading pirated software. Spyware can be distributed by exploits, that promote software piracy.
- Lookout for pop-ups: Malware can lure you into installing spyware on your computer by prompting you with a pop-up window. If you see an unwanted or random pop-up alert, do not click “Agree” or “OK” button to close the pop-up window. This will actually install the malware on your computer. Instead, press Alt + F4 or click on the red “X” on the corner on the pop-up alert to close the window.
- Keep current with operating system updates: Important system updates provide significant benefits such as improved security. Just as with any antivirus and antispyware
software, not keeping up with operating system updates will make your PC vulnerable to the latest malware threats.
- Harden your browser settings: Updated Web browsers may help to prevent exploitation by taking several defensive steps against spyware. Most Web browsers will warn you of executable programs and will suggest a safe course of action. In addition to having an updated Web browser, ensure that you have properly configured your browser and that all of your plug-ins and add-ons are updated, including Java, Flash and Adobe products.
- Enable your firewall: Firewalls monitor the network and are capable of blocking suspicious traffic, which can prevent spyware from infecting your system.
Question. Differentiate between hackers and crackers.
Answer: Differences between hackers and crackers are as follows:
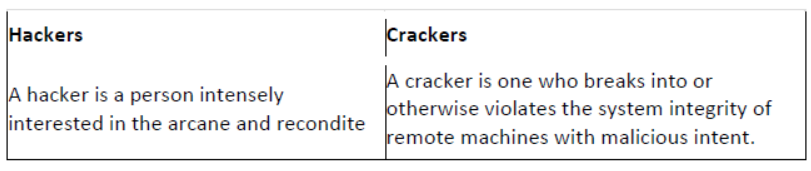
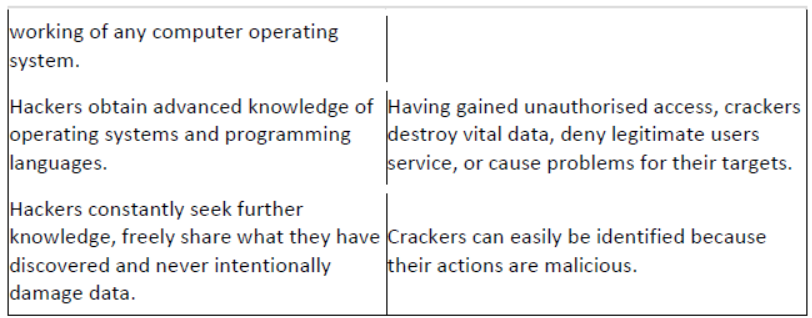
Question. Explain SET, PCI and Kerberos.
Answer:
- PCI (Peripheral Component Interconnect) is a computer bus for attaching hardware devices in a computer. These devices can take either the form of an integrated circuit fitted onto the motherboard itself, called a planer device in the PCI specification or an expansion card that fits into a slot.
- SET (Secure Electronic Transaction) protocol, which is developed by Visa and Mastercard uses encryption for privacy and digital certificates to verify the three parties -the bank, the customer and the merchant. It ensures secure transactions online.
- Kerberos is a third-party authentication that validates the clients over the network and provides secure communication or access to network resources.
Question. Write a short note on social networking.
Answer: It is a grouping of individuals into specific groups, like small rural communities or a neighbourhood subdivision, if you will. A social networking service is an online service, platform or site that focuses on facilitating the building of social networks or social relations among people.
e.g. people who share interests, activities, backgrounds or real life connections. When it comes to online social networking, Websites are commonly used. These Websites are
known as Social Sites. The most popular social sites are currently Facebook, MySpace, Orkut etc.
These Websites provide users with simple tool to create a custom profile with text and pictures. Typical profile includes basic information about user, atleast one photo and possibly a blog or other comments published by the user. It may include videos, photos albums, online applications as in Facebook or custom layout (in MySpace). After creating a profile, user can send message to other users and leave comments directly on friends’ profiles.
Question. Write the benefits of ICT in education and healthcare.
Answer: Benefits of ICT
ICT has become an integral part of our daily life. And, it has benefited the common man in various ways in every field of life. Some of them are as follows:
In Education
The main purpose of the strategy for ICT implementation in education is to provide the prospects and trends of integrating ICT into the general educational activities.
Some benefits of ICT in education are as follows:
1. There is no time boundation on an individual for getting educated by a teacher. A person can attend a class anytime and anywhere.
2. Teachers can create interactive classes and make the lessons more interesting.
3. Generally, students find images and graphical representation of concepts, more interesting as compared, to the theoretical knowledge. And, using ICT, teachers can explain even the most complex concept in a very simplified manner using graphics, videos and animations.
4. An individual can learn on pace he/she is comfortable.
5. Learning resources can be accessed remotely.
In Healthcare
Some benefits of ICT in healthcare are as follows:
1. Automated hospital information systems can help to improve quality of care.
2. Decreased costs of treatment.
3. ICT has significantly enhanced the services being provided and brought behavioural changes.
4. This technology helps doctors, hospitals, the general public and all other medical care providers.
5. Pharmaceutical industry is the industry that enjoys the biggest benefits of ICT.
6. ICT has made E-Health possible.
Question. “Virtual schools are better than traditional schools.” Write reasons to support this statement.
Answer: A virtual school is a learning environment offered entirely on the Internet. All student services and courses are conducted through Internet technology. The virtual school
differs from the traditional school through the physical medium that links administrators, teachers and students. It refers to an institution that is not “brick and mortar” bound.
Advantages
The advantages of virtual schools are as follows:
1. Individualised instruction for all students.
2. Lessons can be taught in a way that benefits students with various learning abilities.
3. More time can be spent on lessons that are more difficult for students.
4. Flexibility for the students to learn whenever and wherever they want.
5. Students are self-directed and mature quicker as they manage their studies.
6. Students can access learning 24 hours a day and learn at their own pace.
Disadvantages
The disadvantages of virtual schools are as follows:
1. Undisciplined students will not succeed in the online environment.
2. Puts more stress on the parents to provide guidance and tutoring.
3. Parents need to monitor the student all day long as opposed to dropping the student
at school where the student is monitored by teachers and staff.
4. Students are more isolated and might not developed properly socially.
5. Students would not receive personal one-on-one time with teachers.
Question. Give one word answer
1. Another name for junk mails.
2. It is doing business online.
3. It is the crime committed using computers and Internet.
4. The programmer that breaks into secure systems with non-malicious intentions.
5. Type of malware that is installed on user’s computer and collects information about user without his consent.
Answer:
1. Spam
2. E-Business/E-Commerce
3. Cyber crime
4. Hacker
5. Spyware
Question. Amit installed an antivirus software to remove all the viruses from his computer.
1. What is antivirus software?
2. Name two actions performed by an antivirus software.
Answer:
1. Antivirus software is used to identify, prevent and take action against malicious programs, such as viruses and worms, by deactivating or deleting them.
2. Two actions performed by an antivirus software are as follows:
(a) Scanning E-mail messages and their attachments.
(b) Scanning and monitoring files and folders on your computer to ensure that they are not infected.
Question. It is an electronic messaging system used by various commercial organisations to send bulk messages to a large number of E-mail addresses. What is it?
1. E-mail
2. Spam
3. SMS
4. Adware
Answer: 2. Spam
Question. Shreenivasan is working for an IT firm where he needs to backup of his data of around 200 MB to 400 MB at the end of each day. Each day backup needs to archived separately for future reference. Suggest any two economic data backup devices, which he can use for this purpose.
Answer: DVD and Pen drive
Question. Mohan has downloaded few attachments in his mail to his system from Internet. When he opened those attachments there were multiple copies of the same file
opened. After sometime his system got rebooted automatically. He is unable to find out why his system is not responding properly. Can you tell what happened to his system and give him some solutions?
Answer: There is a virus (most likely worm) in Mohan’s computer, that has caused damage to data and files on his system. He should install antivirus software, such as Kaspersky, Quick Heal, McAfee etc., as the main defence against online problems. He should take backup of his files regularly.
Question. In a small office network, to protect every computer from hackers, virus or worm. Which statement do you think is True or False from the given options?
1. Set Firewall Turned ON
2. Install antivirus software.
3. Allow users to use external disk drives.
4. Download attachments from reliable source even without scanning.
Answer:
1. True
2. True
3. False
4. False
Multiple Choice Questions
Question. …………… stands for Malicious Software, is software designed to infiltrate a computer system without the owner’s informed consent.
(a) Blog
(b) Attachments
(c) Spam
(d) Malware
Answer: (d) Malware designed to interrupt ongoing computer operations, collect private information and gain unauthorised access to your system resources.
Question. Which one of the following is not a malware?
(a) Computer virus
(b) Spam
(c) Worm
(d) Application software
Answer: (d) Application software refers to the condition in which your computer stops working.
(a) Hang
(b) Virus attack
(c) Hacking
(d) None of these
Answer: (a) Hang refers to the condition in which your computer or a software stops working.
Question. Which of the following is not a symptom of a virus attack?
(a) The computer begins to run slowly
(b) Unusual messages and graphics appear on the screen for inexplicable reasons
(c) Some programs or data files on the computer either become corrupt or are difficult to locate
(d) Your data is copied to another location
Answer: (d) Your data is copied to another location is not a symptom of a virus attack.
Question. A good way to safeguard access to your computer is to protect it.
(a) Deadbolt
(b) Copyright
(c) Safemode
(d) Password
Answer: (d) Password is a good way to safeguard access to your computer to protect it.
Question. Which of the following is the first computer virus?
(a) Brain
(b) Melissa
(c) Elk Cloner
(d) I Love You
Answer: (c) Elk Cloner is the first computer virus created by Richard Skrenta.
Question. Out of the following, which one will be altered or modified by a computer virus?
(a) Operating system
(b) Speed of network connectivity
(c) Application software
(d) All of the above
Answer: (d) All of the above
Question. Which one of the following is not a way to get a computer virus?
(a) Through E-mail attachments
(b) Through pen drive
(c) By typing on keyboard
(d) By downloading files
Answer: (c) By typing on keyboard is not a way to get a computer virus.
Question. The at first glance will appear to be useful software but will actually do damage once installed or run on your computer.
(a) worm
(b) virus
(c) trojan
(d) spam
Answer: (c) The trojans are unauthorised programs placed inside a legitimate application.
Question. A …….. is a virus that is often disguised as a useful computer program.
(a) trojan horse
(b) hacker
(c) worm
(d) spam
Answer: (a) Trojan horse is a virus, i.e. often disguised as a useful computer program.
Question. A ……. is a software program that is designed to copy itself from one computer to another, without human intervention.
(a) trojan
(b) vims
(c) worm
(d) spam
Answer: (c) A worm is a self-replicating software program. It does not require another program to host it.
Question. Which of the following is not an example of worm?
(a) MS-Blaster
(b) Sobig
(c) De bumper
(d) Melissa
Answer: (c) De bumper is a type of trojan horse.
Question. Which of the following statements is incorrect in the context of a worm?
(a) It represents a category of malware
(b) It creates infections in a computer
(c) It is self replicating
(d) It cannot travel on its own
Answer: (d) Worm is self replicating software and thus, it can travel on its own.
Question. A category of software that spies of your computer activities is
(a) De-ware
(b) Spyware
(c) Utilities
(d) Freeware
Answer: (b) Spyware is a category of software that spies computer activities.
Question. The electronic equivalent of junk mail is known as
(a) adware
(b) cyber fraud
(c) spam
(d) packets
Answer: (c) Spam is an electronic equivalent of junk mail.
Question. Which of the following is not antivirus software?
(a) Norton Antivirus
(b) Melissa
(c) McAfee
(d) SmartCop
Answer: (b) Melissa is a macro virus, not an antivirus.
Question. To avoid problems while working on the Internet, you should follow these precautions.
(a) Install antivirus on your computer
(b) Take the backup of your files regularly
(c) Do not click on unknown links
(d) All of the above
Answer: (d) All of the above
Question. One limitation of antivirus programs is that they:
(a) Sometimes start behaving like virus
(b) Are very expensive
(c) Harm the computer
(d) Can detect only those viruses for which they are programmed
Answer: (d) Antivirus can detect only those viruses for which they are programmed.
Question. The programmers who break into secure systems for malicious purpose are
(a) crackers
(b) hackers
(c) breakers
(d) burglars
Answer: (a) Crackers are the programmers that break into secure systems for malicious purpose.
Question. A is someone who breaks into someone else’s computer system, often on a network; bypasses passwords or licenses in computer programs without malicious intent with a wish to learn and improve security.
(a) hacker
(b) cracker
(c) worm
(d) malware
Answer: (a) A hacker is a person who enjoys learning programming languages and about computer systems and their working.
Question. A digital document issued to a Website by a certification authority on the Internet is called
(a) digital signature
(b) encryption
(c) digital certificate
(d) firewall
Answer: (c) A digital certificate is an electronic file that is issued by a certification authority to Websites.
Question. You can transmit sensitive information, such as that relating to your credit card, by using
(a) PCI
(b) SET
(c) SSL
(d) Firewall
Answer: (c) SSL allows sensitive information such as credit card numbers to be transmitted securely.
Question. Firewall:
(a) Amplifies weak outgoing signals to stronger ones
(b) Is the name of an open source browser
(c) Is the name of computer virus
(d) Prevents intruders from accessing your system
Answer: (d) A firewall can either be software based or hardware based and is used to prevent intruders from accessing your system.
Fill in the Blanks [1 Mark each]
Question. ………… is the general term to refer to infectious software such as virus, worm, spyware etc.
Answer: Malware
Question. A malicious program that is used to remove all information from your computer is known as ………
Answer: sweeper
Question. A ……….. infects the files of the operating system.
Answer: boot sector virus
Question. ……. and ………. are the two types of malware.
Answer: Viruses, Worms
Question. ……….. can decrease the space on hard disks by duplicating files.
Answer: Viruses
Question. ……… is a program that appears harmless but actually performs malicious functions.
Answer: Trojan horse
Question. ……….. is a software program that is designed to copy itself from one computer to another.
Answer: Worm
Question. Unlike a computer virus, a ……….. can replicate itself automatically.
Answer: worm
Question. …………. is a type of malware that is installed on a user’s computer and collects information about user without their consent and knowledge.
Answer: Spyware
Question. Any crime committed using computers and Internet is termed as …………
Answer: cyber crime
Question. ………. attack eats up all the resources of a system and halts it.
Answer: Denial of service
Question. ……… is a computer program that detects, prevents and takes action to remove malicious software programs.
Answer: Antivirus
Question. Copy of data created for safe storage is …………
Answer: backup
Question. ………… backup saves your data from natural disasters.
Answer: Online
Question. ……. is a type of backup in which only the data that changed, since last backup is saved.
Answer: Differential backup
Question. A digital code attached to an electronic message to provide it unique identity is called…………
Answer: digital signature
Question. ………. security technology establishes an encrypted link between a Web server and browser.
Answer: SSL
Question. …… refers to the disparity of classification of person according to their knowledge of ICT and without it.
Answer: Digital divide
True or False
Question. A virus may corrupt or delete data on your computer.
Answer: True A virus may corrupt or delete data on your computer.
Question. A virus is a harmful program, which one entering a computer, starts creating copies of itself.
Answer: True Virus is a malicious program that is designed to make a system sick, just like a real virus.
Question. A worm is a self-replicating program which eats up the entire disk space.
Answer: False Virus eats up the entire disk space.
Question. Spyware is a type of malware but is not capable of collecting personal information.
Answer: False Spyware is a type of malware used to collect personal information without his or her knowledge.
Question. Adware is a ‘Software that posts unwanted advertisements on your computer.
Answer: True Adware is a software that is given to the user with unwanted advertisements embedded in the application.
Question. Always scan the storage media before connecting it to your computer.
Answer: True You should always scan your storage media before connecting it to your computer.
Question. SmartCop is an antivirus developed in India.
Answer: True SmartCop antivirus is developed in India.
Question. Junk E-mails are also called spam.
Answer: True E-mail spam, junk mail or junk newsgroup posting is a widely recognised form of spam.
Question. Cracker is a person who breaks security to see what we have stored on our computers with mat intentions.
Answer: True Cracker breaks security with mal intentions.
Question. It is not necessary to regularly take back-up of important files.
Answer: False A backup ensures that your computer data is protected or can be recovered.
Question. CD is a storage device that is used to take the backup of your data.
Answer: True You can use different types of storage devices like CD, DVD to take the backup of your data.
Question. You cannot keep the backup of your data online.
Answer: False In online backup, you send the data to a remote server through the Internet.
Question. Backup is duplication of data for restoring purpose at a later time.
Answer: True Backup is a process to copy the data and restore it, whenever required.
Question. SET is a protocol developed by Visa and Mastercard.
Answer: True SET is a protocol developed by Visa and Mastercard. It ensures secure transactions over the Internet.
| NCERT Solutions Class 10 Computers Database Concepts |
| NCERT Solutions Class 10 Computers Database Management System |
| NCERT Solutions Class 10 Computers Digital Documentation Advanced |
| NCERT Solutions Class 10 Computers Electronic Spreadsheet Advanced |
| NCERT Solutions Class 10 Computers Entrepreneurial Skills II |
| NCERT Solutions Class 10 Computers Inserting Images and Links in HTML |
| NCERT Solutions Class 10 Computers Internet Basics |
| NCERT Solutions Class 10 Computers Internet Services |
| NCERT Solutions Class 10 Computers Introduction to XML |
| NCERT Solutions Class 10 Computers Microsoft Access |
| NCERT Solutions Class 10 Computers Societal Impacts of IT |
| NCERT Solutions Class 10 Computers Web Applications and Security |
| NCERT Solutions Class 10 Computers Working with Tables in HTML |
Important Practice Resources for Class 10 Computers
NCERT Solutions Class 10 Computers Societal Impacts of IT
Students can now access the NCERT Solutions for Societal Impacts of IT prepared by teachers on our website. These solutions cover all questions in exercise in your Class 10 Computers textbook. Each answer is updated based on the current academic session as per the latest NCERT syllabus.
Detailed Explanations for Societal Impacts of IT
Our expert teachers have provided step-by-step explanations for all the difficult questions in the Class 10 Computers chapter. Along with the final answers, we have also explained the concept behind it to help you build stronger understanding of each topic. This will be really helpful for Class 10 students who want to understand both theoretical and practical questions. By studying these NCERT Questions and Answers your basic concepts will improve a lot.
Benefits of using Computers Class 10 Solved Papers
Using our Computers solutions regularly students will be able to improve their logical thinking and problem-solving speed. These Class 10 solutions are a guide for self-study and homework assistance. Along with the chapter-wise solutions, you should also refer to our Revision Notes and Sample Papers for Societal Impacts of IT to get a complete preparation experience.
The complete and updated is available for free on StudiesToday.com. These solutions for Class 10 Computers are as per latest NCERT curriculum.
Yes, our experts have revised the as per 2026 exam pattern. All textbook exercises have been solved and have added explanation about how the Computers concepts are applied in case-study and assertion-reasoning questions.
Toppers recommend using NCERT language because NCERT marking schemes are strictly based on textbook definitions. Our will help students to get full marks in the theory paper.
Yes, we provide bilingual support for Class 10 Computers. You can access in both English and Hindi medium.
Yes, you can download the entire in printable PDF format for offline study on any device.

